New updates
Unless otherwise indicated, the features below are fully launched or in the process of rolling out (rollouts should take no more than 15 business days to complete), launching to both Rapid and Scheduled Release at the same time (if not, each stage of rollout should take no more than 15 business days to complete), and available to all legacy Google Workspace and G Suite customers.
Find and insert GIFs faster on Google Chat on iOS Devices
You can now easily browse, select and insert GIFs while using the Chat iOS mobile app. When enabled by your admin, select the “GIF” icon in the Google Chat compose bar. We hope this makes it easier for you to express yourself when interacting with your colleagues. |
Learn more.
Set a custom duration for "Do Not Disturb" in Google Chat on web and iOS devices
You can now set the duration of your "Do Not Disturb" status to a specific date and time. We hope this feature gives you the flexibility to mute notifications the way it best suits you. This feature is now available on web, Android and iOS devices. |
Learn more.
Previous announcements
The announcements below were published on the Workspace Updates blog earlier this week. Please refer to the original blog posts for complete details.
New admin controls for access to discoverable spaces in Google Chat
We’ve added the ability for Admins to set the default for newly created spaces and enable sharing scoped to specific audiences. |
Learn more.
Available to Google Workspace Business Plus, Enterprise Standard, Enterprise Plus, Education Plus, and Education Standard customers.
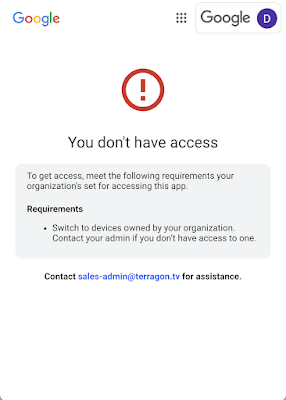
Context-Aware Access remediator provides more context for access denials
Admins using
Context-Aware Access can now provide more information to end users when their access is blocked using the user remediation feature. |
Learn more.
Available to Google Workspace Enterprise Plus, Education Plus, and Cloud Identity Premium customers.
Mark your important tasks with a star in Google Tasks
You can now mark important tasks with a star in Google Tasks. Additionally, you’ll be able to view or sort your starred items across various tasks lists in the new starred view. |
Learn more.
.png)








.png)
.png)