
In October 2024, we announced that Chrome 131 will allow third-party autofill services on Android (like password managers) to natively autofill forms on websites. Reflecting on feedback from autofill service developers, we've decided to shift the schedule and allow the third-party autofill services from Chrome 135.
Native Chrome support for third-party autofill services on Android means that users will be able to use their preferred password manager or autofill service directly in Chrome, without having to rely on workarounds or extensions. This change is expected to improve the user experience and security for Android users who use third-party autofill services.
Based on developer feedback, we've fixed bugs, and have been working to make the new setting easier to discover. To support those goals, we've added the following capabilities:
- An ability to query Chrome settings and learn whether the user wishes to use a third party autofill service
- An ability to deep link to the Chrome settings page where users can enable third-party autofill services.
Read Chrome settings
Any app can read whether Chrome uses the 3P autofill mode that allows it to use Android Autofill. Chrome uses Android's ContentProvider to communicate that information. Declare in your Android manifest which channels you want to read settings from, e.g.:
<uses-permission android:name="android.permission.READ_USER_DICTIONARY"/> <queries> <!-- To Query Chrome Beta: --> <package android:name="com.chrome.beta" /> <!-- To Query Chrome Stable: --> <package android:name="com.android.chrome" /> </queries>
Then, use Android's ContentResolver to request that information by building the content URI as in this example code:
final String CHROME_CHANNEL_PACKAGE = "com.android.chrome"; // Chrome Stable. final String CONTENT_PROVIDER_NAME = ".AutofillThirdPartyModeContentProvider"; final String THIRD_PARTY_MODE_COLUMN = "autofill_third_party_state"; final String THIRD_PARTY_MODE_ACTIONS_URI_PATH = "autofill_third_party_mode"; final Uri uri = new Uri.Builder() .scheme(ContentResolver.SCHEME_CONTENT) .authority(CHROME_CHANNEL_PACKAGE + CONTENT_PROVIDER_NAME) .path(THIRD_PARTY_MODE_ACTIONS_URI_PATH) .build(); final Cursor cursor = getContentResolver().query( uri, /*projection=*/new String[] {THIRD_PARTY_MODE_COLUMN}, /*selection=*/ null, /*selectionArgs=*/ null, /*sortOrder=*/ null); cursor.moveToFirst(); // Retrieve the result; int index = cursor.getColumnIndex(THIRD_PARTY_MODE_COLUMN); if (0 == cursor.getInt(index)) { // 0 means that the third party mode is turned off. Chrome uses its built-in // password manager. This is the default for new users. } else { // 1 means that the third party mode is turned on. Chrome uses forwards all // autofill requests to Android Autofill. Users have to opt-in for this. }
Deep-link to Chrome settings
To deep-link to the Chrome settings page where users can enable third-party autofill services, use an Android Intent. Ensure to configure the action and categories exactly as in this example code:
Intent autofillSettingsIntent = new Intent(Intent.ACTION_APPLICATION_PREFERENCES); autofillSettingsIntent.addCategory(Intent.CATEGORY_DEFAULT); autofillSettingsIntent.addCategory(Intent.CATEGORY_APP_BROWSER); autofillSettingsIntent.addCategory(Intent.CATEGORY_PREFERENCE); // Invoking the intent with a chooser allows users to select the channel they want to // configure. If only one browser reacts to the intent, the chooser is skipped. Intent chooser = Intent.createChooser(autofillSettingsIntent, "Pick Chrome Channel"); startActivity(chooser); // If the caller knows which Chrome channel they want to configure, // they can instead add a package hint to the intent, e.g. autofillSettingsIntent.setPackage("com.android.chrome"); startActivity(autofillSettingsInstent);
Updated timeline
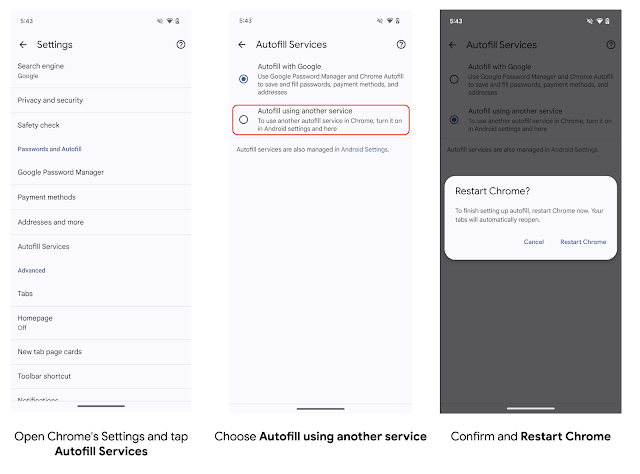
To reflect the feedback and to leave time for autofill service developers to make relevant changes, we are shifting the plan. Users must select Autofill using another service in Chrome settings to ensure their autofill experience is unaffected. The new setting will become available in Chrome 135. Autofill services should encourage their users to toggle the setting, to ensure they have the best autofill experience possible with their service and Chrome on Android. Chrome plans to stop supporting the compatibility mode in summer 2025.
- March 5th, 2025: Chrome 135 beta is available
- April 1st, 2025: Chrome 135 is in stable
- Summer 2025: Compatibility mode will no longer be available on Chrome
 Posted by
Posted by  Posted by Joseph Lewis – Android Developer Relations Technical Writer, and Niharika Arora – Android Developer Relations Engineer
Posted by Joseph Lewis – Android Developer Relations Technical Writer, and Niharika Arora – Android Developer Relations Engineer

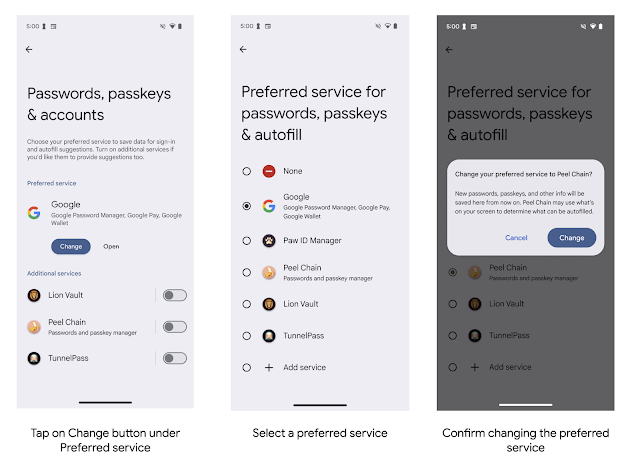
 Posted by Christiaan Brand – Group Product Manager
Posted by Christiaan Brand – Group Product Manager

 Posted by Vikrant Rana, Product Manager
Posted by Vikrant Rana, Product Manager



 Posted by
Posted by 
.png)
.png)
.png)
.png)