What’s changing
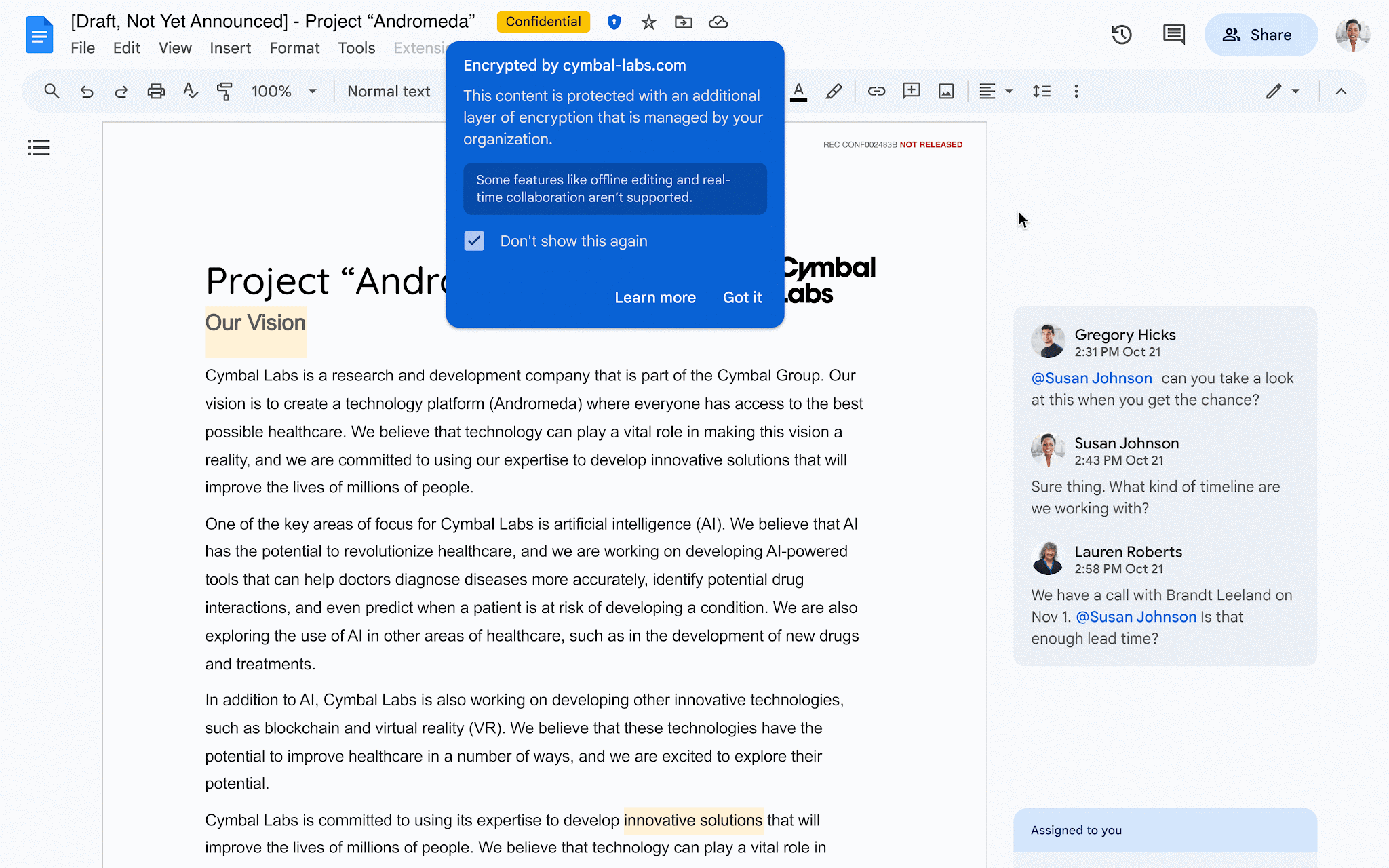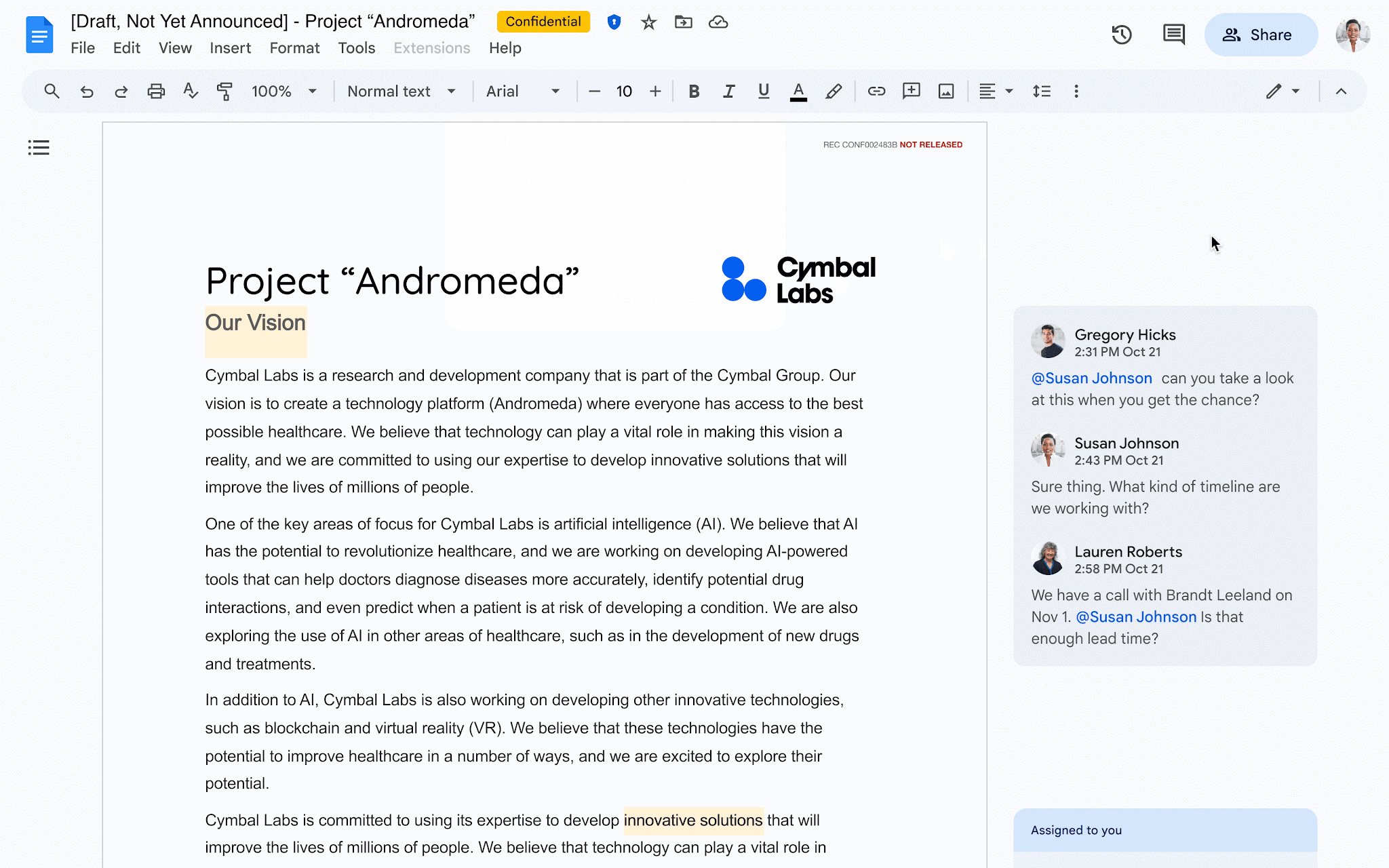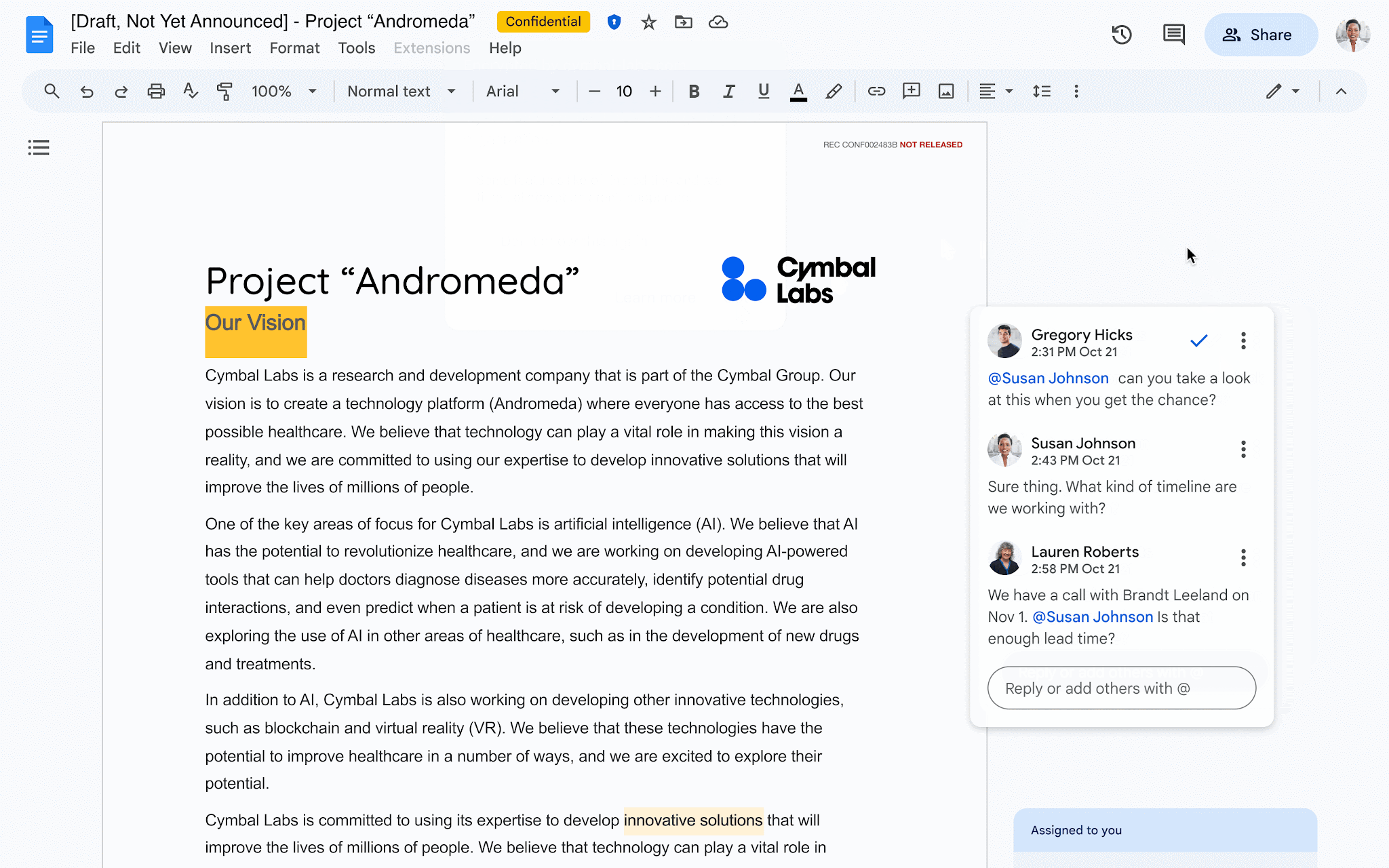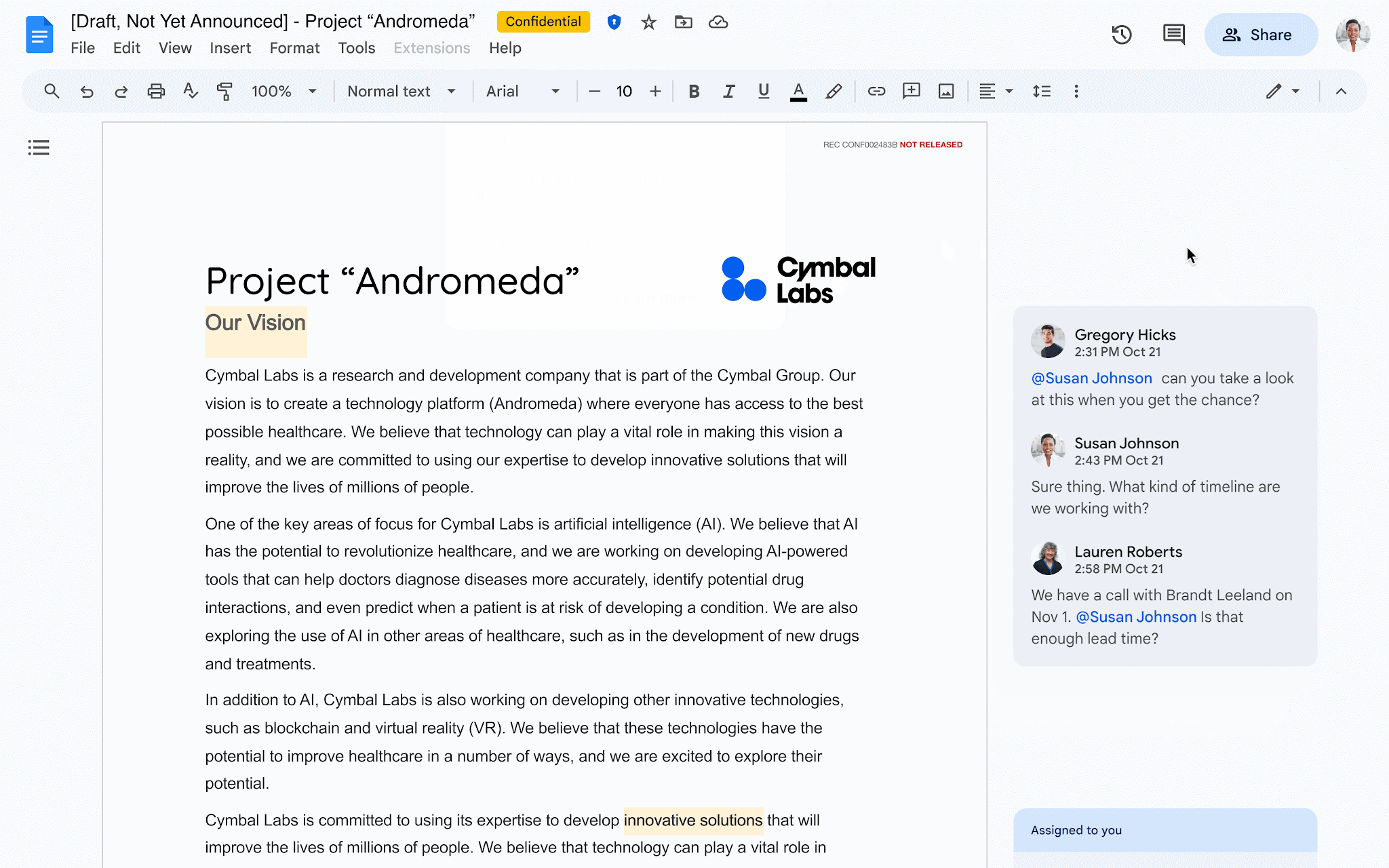
You can now collaborate with others on client-side encrypted Google Docs to add, edit, reply, filter, or delete comments. You can also assign action items to yourself or others. This added functionality helps bring parity to unencrypted docs while also ensuring your data is behind encryption keys you control, including the identity provider used to access those keys.
This feature is available as an open beta, which means you can use it without enrolling in a specific beta program. While this feature is available for Google Docs initially, with support coming for Google Sheets and Slides in the future.
Additional details
Note that when sharing encrypted files, you can only assign “viewer” or “editor” permissions — the “comment only” permission is not supported.
Comments are saved each time the document is autosaved. If you restore the document to a previous version, the comments added to the document in that version are also restored.
Getting started
Rollout pace
Availability
- Available to Google Workspace Enterprise Plus, Education Standard and Education Plus customers
Resources