Nearly half of third-parties fail to meet two or more of the Minimum Viable Secure Product controls. Why is this a problem? Because "98% of organizations have a relationship with at least one third-party that has experienced a breach in the last 2 years."
In this post, we're excited to share the latest improvements to the Minimum Viable Secure Product (MVSP) controls. We'll also shed light on how adoption of MVSP has helped Google improve its security processes, and hope this example will help motivate third-parties to increase their adoption of MVSP controls and thus improve product security across the industry.
About MVSP
In October 2021, Google publicly launched MVSP alongside launch partners. Our original goal remains unchanged: to provide a vendor-neutral application security baseline, designed to eliminate overhead, complexity, and confusion in the end-to-end process of onboarding third-party products and services. It covers themes such as procurement, security assessment, and contract negotiation.
Improvements since launch
As part of MVSP’s annual control review, and our core philosophy of evolution over revolution, the working group sought input from the broader security community to ensure MVSP maintains a balance between security and achievability.
As a result of these discussions, we launched updated controls. Key changes include: expanded guidance around external vulnerability reporting to protect bug hunters, and discouraging additional costs for access to basic security features – inline with CISA’s "Secure-by-Design" principles.
In 2022, we developed guidance on build process security based on SLSA, to reflect the importance of supply chain security and integrity.
From an organizational perspective, in the two years since launching, we've seen the community around MVSP continue to expand. The working group has grown to over 20 global members, helping to diversify voices and broaden expertise. We've also had the opportunity to present and discuss the program with a number of key groups, including an invitation to present at the United Nations International Computing Centre – Common Secure Conference.

Google at the UNICC conference in Valencia, Spain
How Google uses MVSP
Since its inception, Google has looked to integrate improvements to our own processes using MVSP as a template. Two years later, we can clearly see the impact through faster procurement processes, streamlined contract negotiations, and improved data-driven decision making.
Highlights
After implementing MVSP into key areas of Google's third-party life-cycle, we've observed a 68% reduction in the time required for third-parties to complete assessment process.
By embedding MVSP into select procurement processes, Google has increased data-driven decision making in earlier phases of the cycle.
Aligning our Information Protection Addendum’s safeguards with MVSP has significantly improved our third-party privacy and security risk management processes.
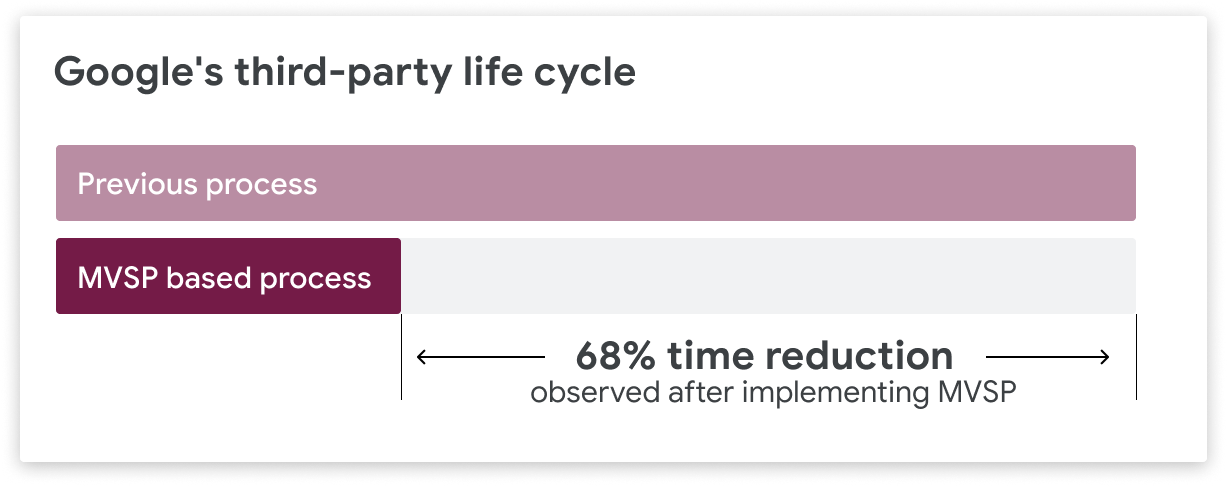
You use MVSP to enhance your software or procurement processes by reviewing some common use-cases and adopting them into your third-party risk management and/or contracting workflows .
What's next?
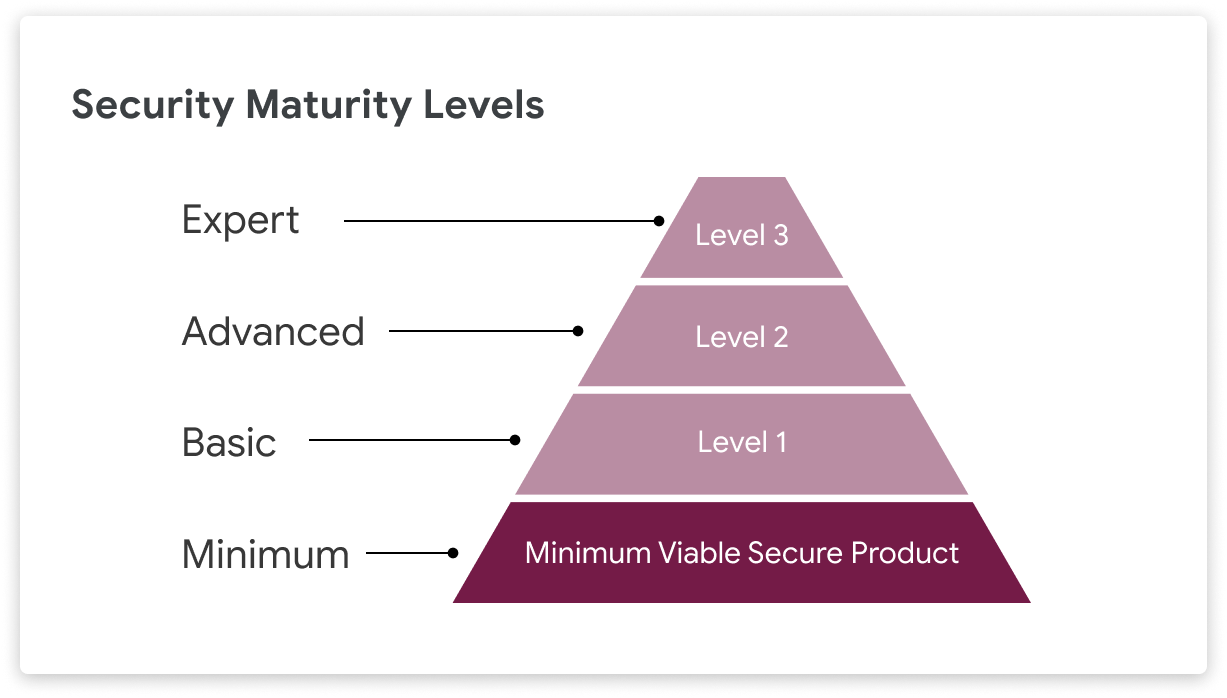
We're invested in helping the industry manage risk posture through continuous improvement, while increasing the minimum bar for product security across the industry.
By making MVSP available to the wider industry, we are helping to create a solid foundation for growing the maturity level of products and services. Google has benefited from driving security and safety improvements through the use of leveled sets of requirements. We expect the same to be true across the wider industry.
We've seen success, but there is still work to be done. Based on initial observations, as mentioned above, 48% of third-parties fail to meet two or more of the Minimum Viable Secure Product controls.
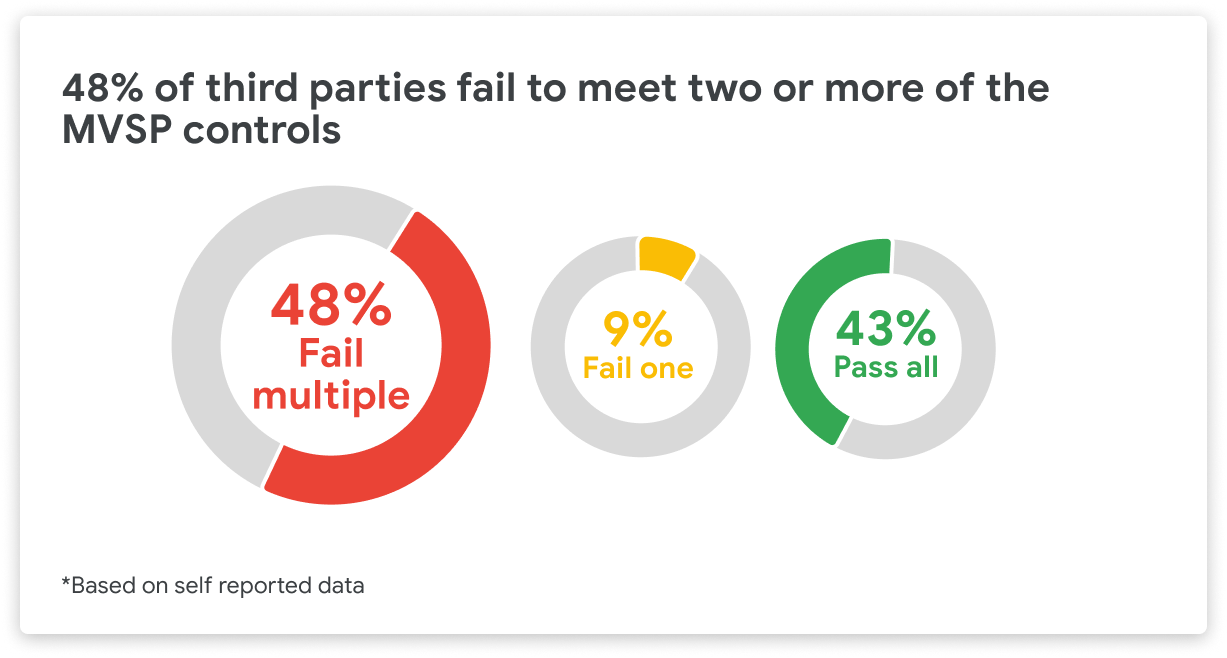
As an industry, we can't stand still when it comes to product security. Help us raise the minimum bar for application security by adopting MVSP and ensuring we as an industry don’t accept anything less than a strong security baseline that works for the wider industry.
Acknowledgements
Google and the MVSP working group would like to thank those who have supported and contributed since its inception. If you'd like to get involved or provide feedback, please reach out.
Thank you to Chris John Riley, Gabor Acs-Kurucz, Michele Chubirka, Anna Hupa, Dirk Göhmann and Kaan Kivilcim from the Google MVSP Group for their contributions to this post.
 "Artetik: From the Art" is a groundbreaking digital experience around art and emotions, the result of a new collaboration between the Guggenheim Museum Bilbao and Google…
"Artetik: From the Art" is a groundbreaking digital experience around art and emotions, the result of a new collaboration between the Guggenheim Museum Bilbao and Google…
 "Artetik: From the Art" is a groundbreaking digital experience around art and emotions, the result of a new collaboration between the Guggenheim Museum Bilbao and Google…
"Artetik: From the Art" is a groundbreaking digital experience around art and emotions, the result of a new collaboration between the Guggenheim Museum Bilbao and Google…




 Immerse yourself in India’s movie making culture through an interactive exhibit with 7,000 artifacts, 120 stories, virtual tours of iconic cinemas, a puzzle party game a…
Immerse yourself in India’s movie making culture through an interactive exhibit with 7,000 artifacts, 120 stories, virtual tours of iconic cinemas, a puzzle party game a…
 Check out the redesigned Chrome Web Store with new categories and improved navigation to help you easily personalize your browser.
Check out the redesigned Chrome Web Store with new categories and improved navigation to help you easily personalize your browser.
 Android Enterprise helped IIFL Finance securely scale mobile device management for their 18,000 employees.
Android Enterprise helped IIFL Finance securely scale mobile device management for their 18,000 employees.

 Google's fourth annual Black-owned Friday encourages everyone to support, search for and shop from Black-owned businesses.
Google's fourth annual Black-owned Friday encourages everyone to support, search for and shop from Black-owned businesses.
 Try out a new small business filter, compare deals from across the web and get AI-generated gift ideas.
Try out a new small business filter, compare deals from across the web and get AI-generated gift ideas.
 AI has the potential to mitigate 5-10% of global greenhouse gas emissions according to our new report with Boston Consulting Group.
AI has the potential to mitigate 5-10% of global greenhouse gas emissions according to our new report with Boston Consulting Group.