What’s changing
Today, we are announcing enhancements for the
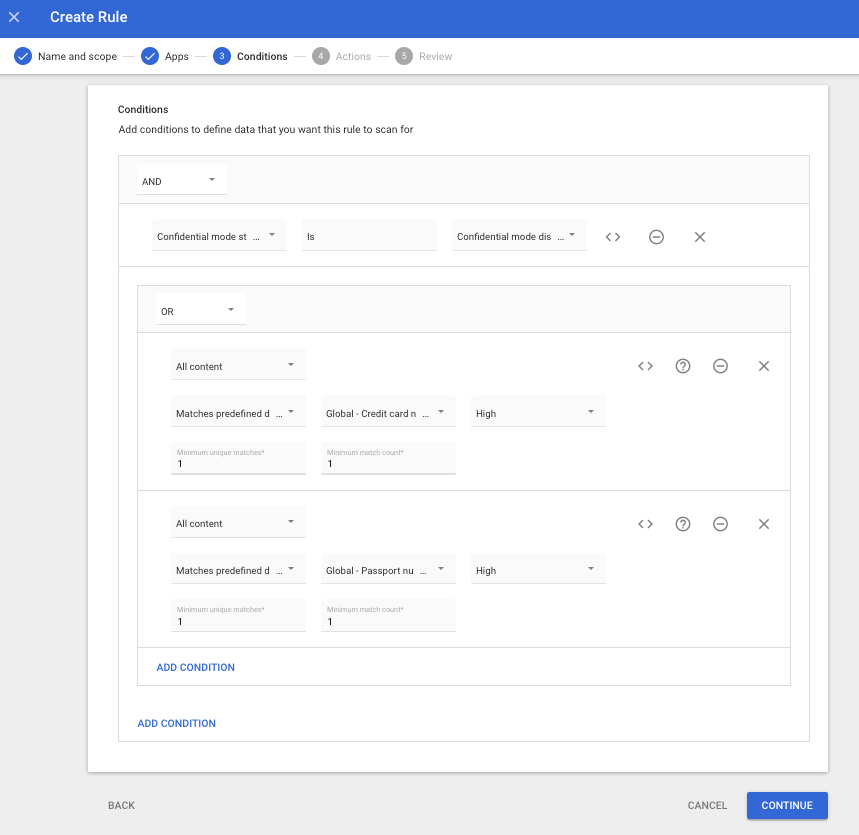
Data Loss Prevention for Gmail open beta, which are designed to improve usability without compromising sensitive data protections for Gmail. Once deployed, users will receive instant notifications on risks to applicable DLP policies prior to leaving their inbox, instead of having DLP rules evaluated after the message has already left the inbox. In addition to more timely user feedback, this capability, called synchronous DLP, helps educate users about the potential risk of leaking sensitive information.
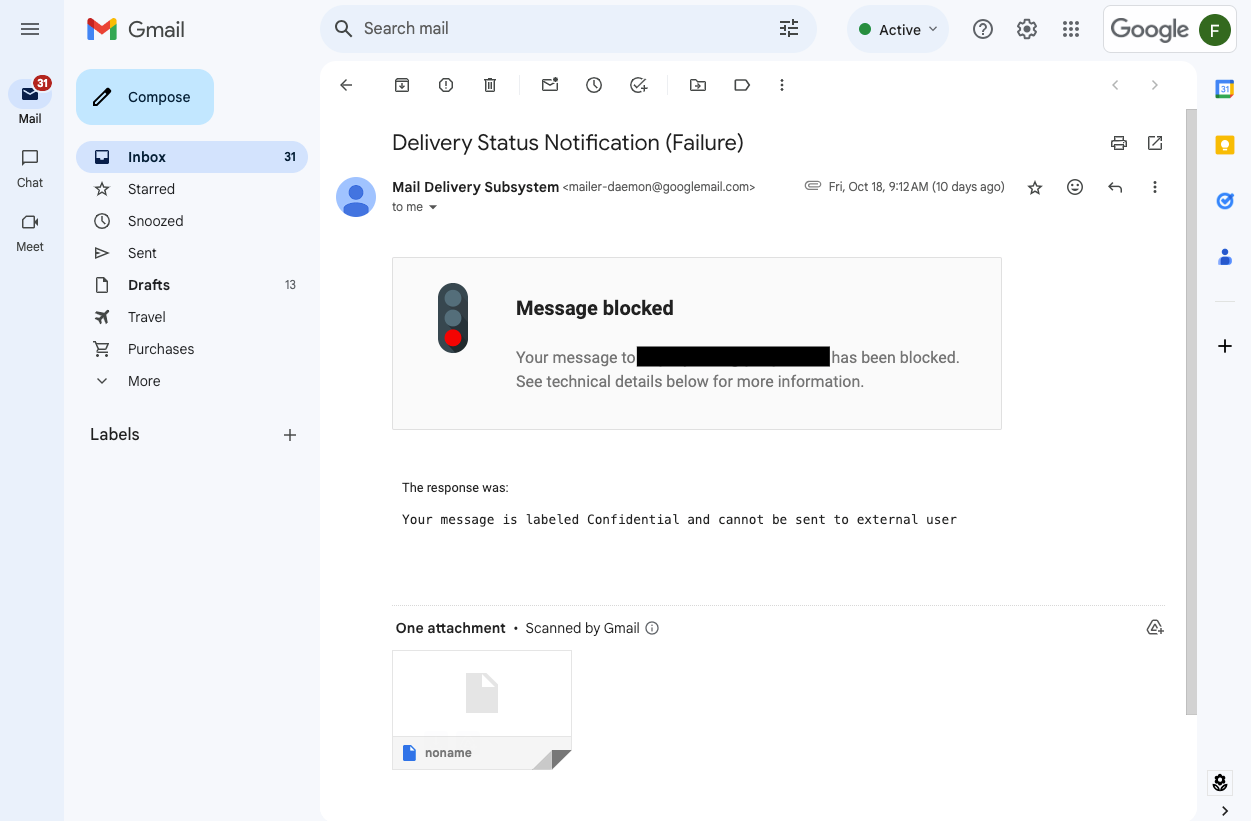
We’re also introducing a new action for DLP rules, “Warn”, which will notify users about potentially sensitive data while providing the option to send the message based on a user’s assessment of a risk. For added safety, the DLP service will scan messages one additional time after they leave the sender's mailbox.
Who’s impacted
Admins and end users
Why it matters
Data breaches are one of the most common and costly security issues facing organizations. Often these breaches originate from within an organization by unintentional or intentional actions by their users. Data loss prevention capabilities help prevent this exfiltration of data and helps guide users about what information to share. To help safeguard sensitive information, organizations can create and enforce policies that not only detect and block sensitive information from being shared, but educate users on what information sharing is or is not appropriate and how to be compliant with those guidelines. Specifically, data loss prevention rules can look for sensitive text stings, custom detectors, or predefined detectors in outgoing messages sent internally or externally.
The latest update for data loss prevention rules in Gmail brings the experience in line with Google Drive and Google Chat, which are already adopted broadly by Google Workspace customers. You can refer to our Help Center for more information about
data loss prevention in Gmail.
Additional details
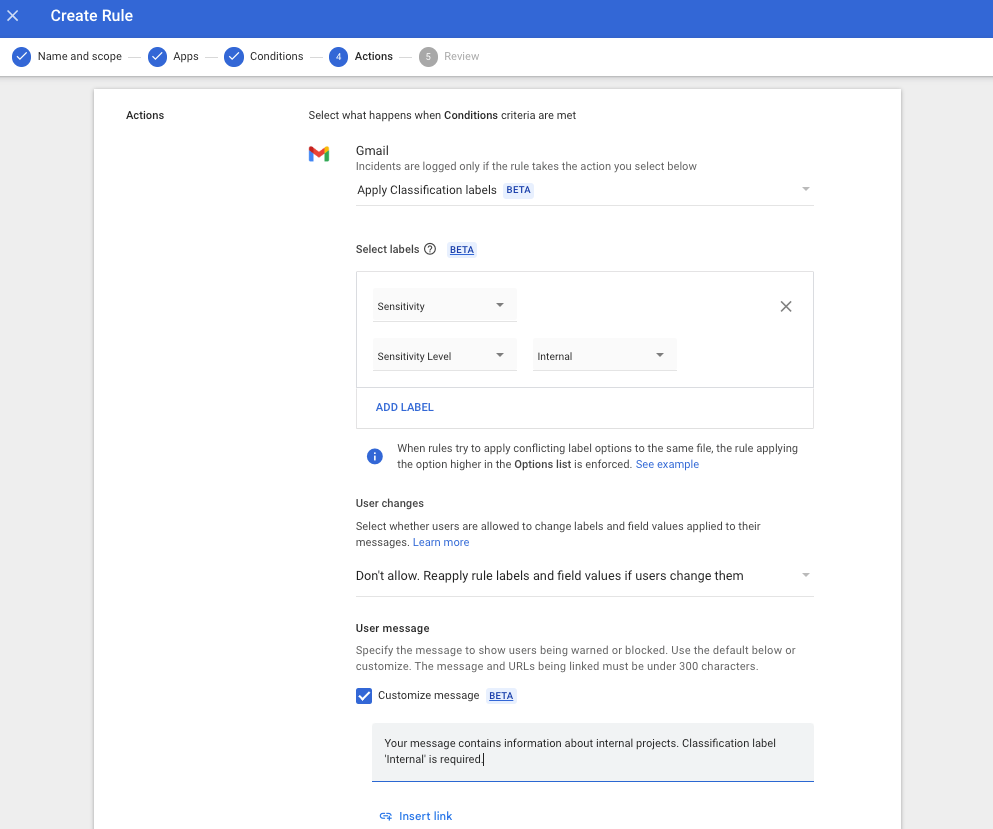
Customizable warning messages
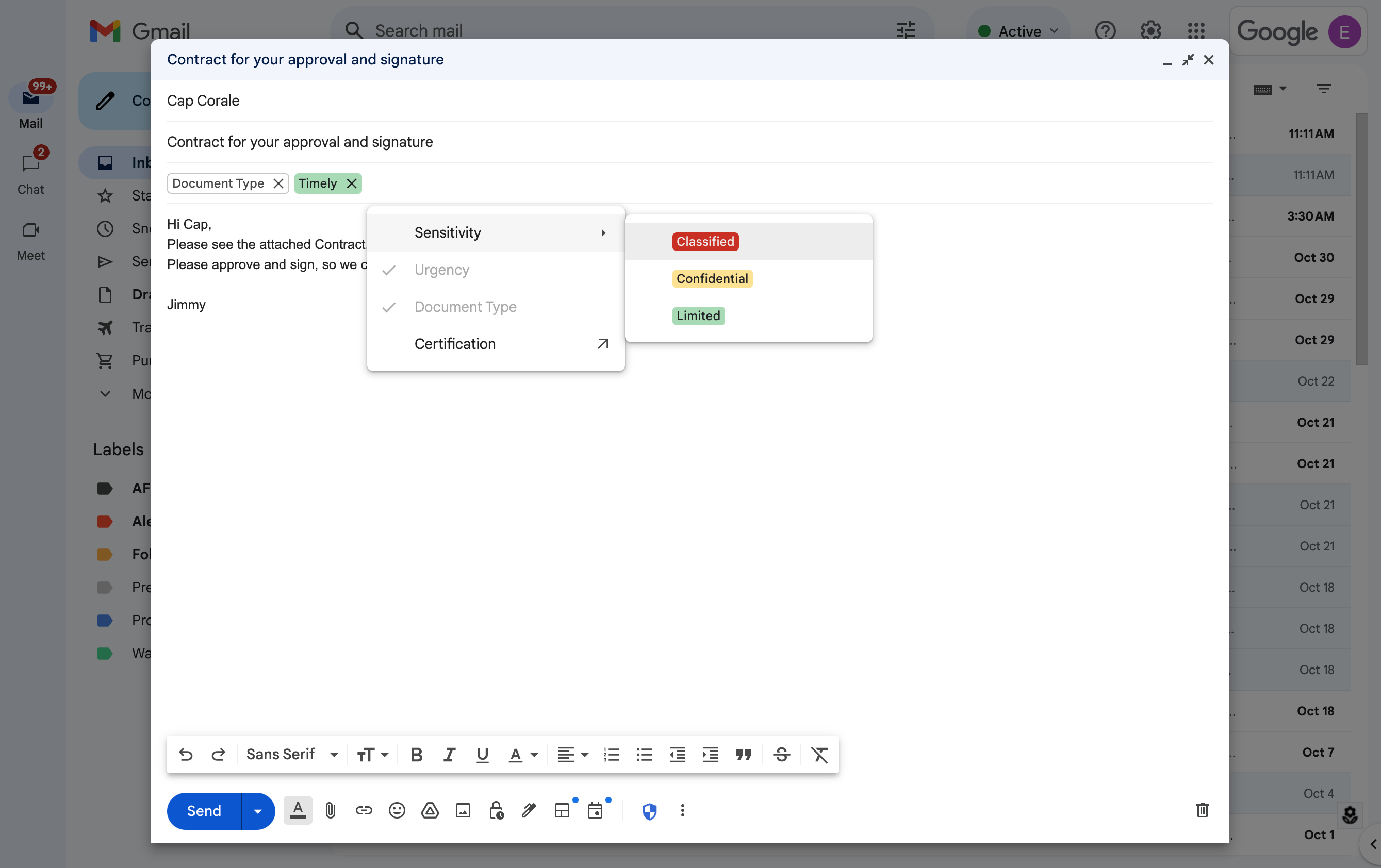
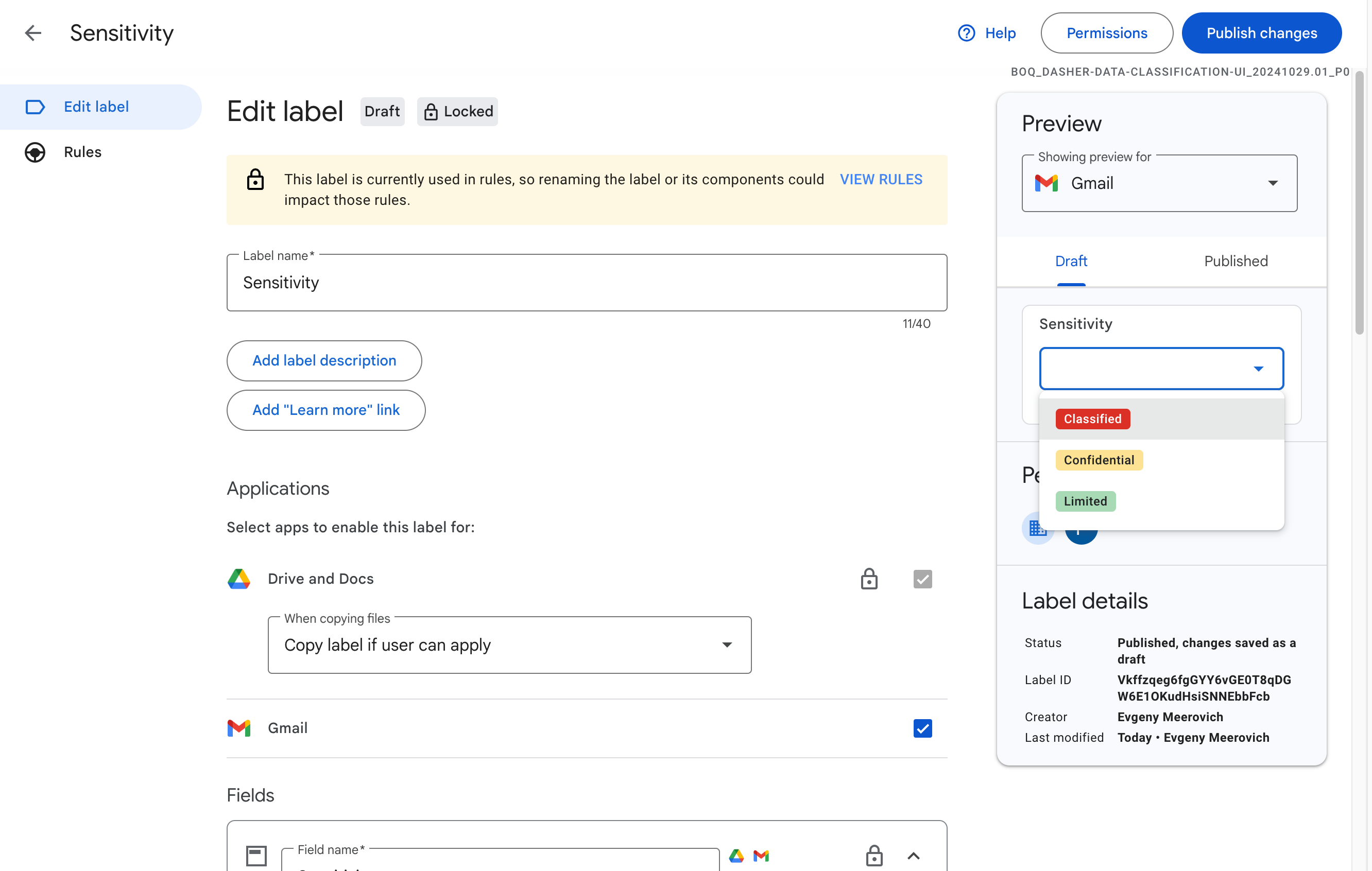
DLP rules can be configured to block the message, warn users about sensitive information, or quarantine the message. When sensitive information is detected, users will be shown a dialog box notifying them of the risk. Admins can now choose to customize the information shown to end users in these dialog boxes, including why their message was flagged, what they can do to unblock themselves, and links to additional resources to educate them further.
Example of a custom warning message
Continued asynchronous scanning of messages
While messages will now be scanned synchronously, messages will go through additional scanning asynchronously (after the message leaves the inbox) for an additional layer of protection. This includes messages that are sent automatically, such as auto-forward or scheduled send, and messages sent from non-Gmail clients.
Rollout pace
Availability
Available for Google Workspace:
- Enterprise Standard, Enterprise Plus
- Education Fundamentals, Standard, Plus, and the Teaching & Learning Upgrade
- Frontline Standard
- Cloud Identity Premium customers
Resources



.png)