Posted by Jamal Eason, Product Manager, Android
Today, Android Studio 3.2 is available for download. Android Studio 3.2 is the best way for app developers to cut into the latest Android 9 Pie release and build the new Android App bundle. Since announcing this update of Android Studio at Google I/O '18, we have refined and polished 20+ new features and focused our efforts on improving the quality for this stable release of Android Studio 3.2.
Every developer should use Android Studio 3.2 to transition to using an Android App Bundle, the new app publishing format. With very minimal work, you can generate an app bundle with Android Studio. Once you upload your app bundle to Google Play you can distribute smaller, optimized apps to your users. Early adopters have already seen between 11% - 64% in app size savings with app bundles over the legacy APK app size.
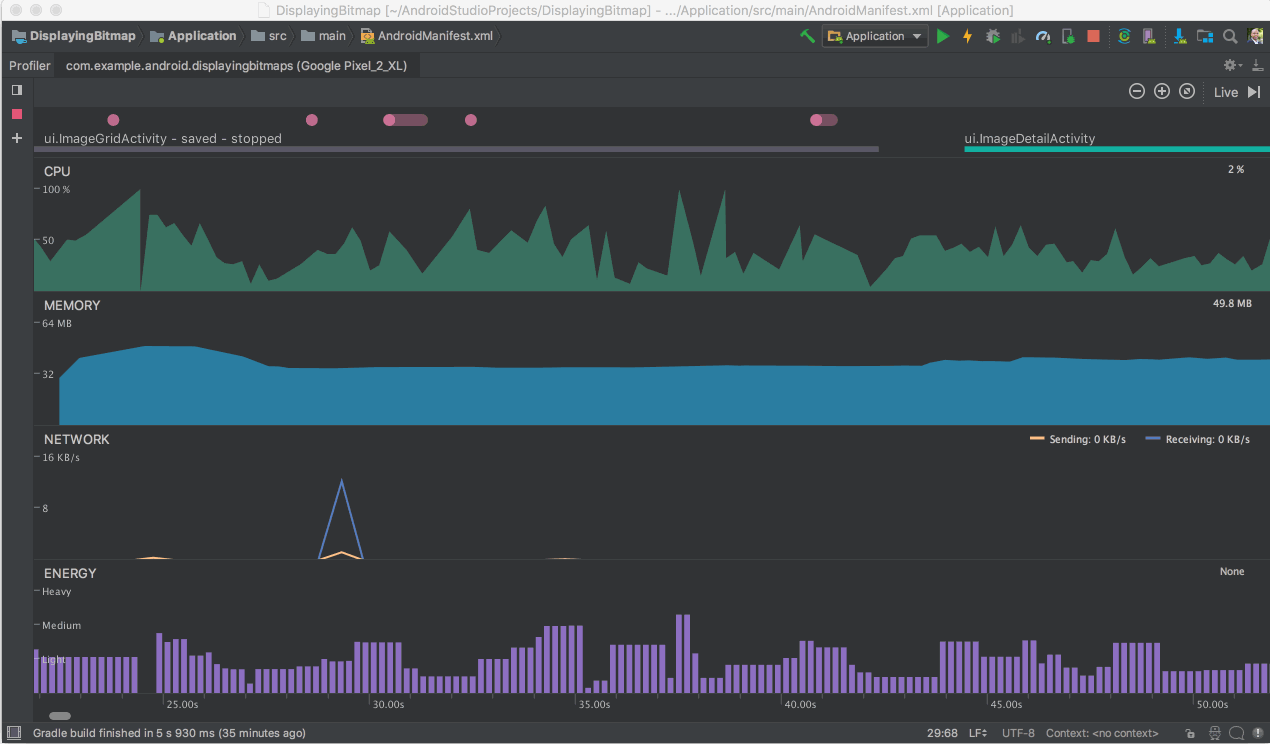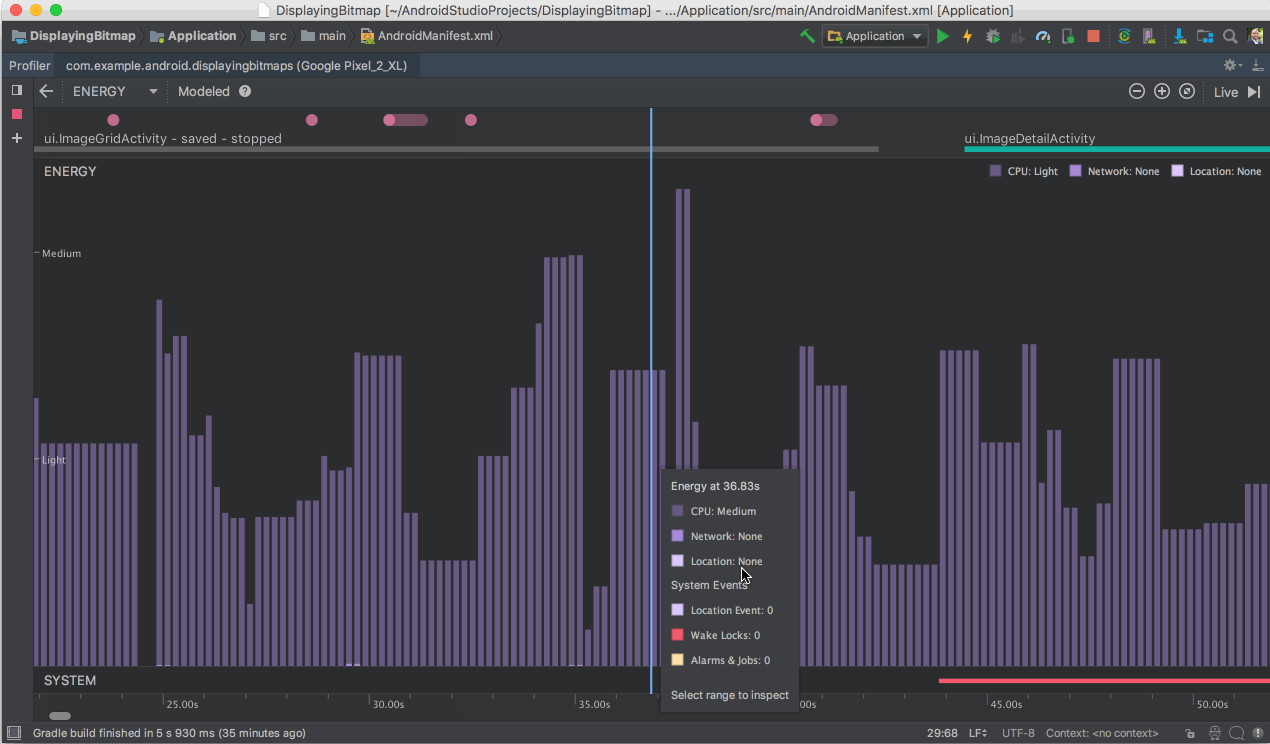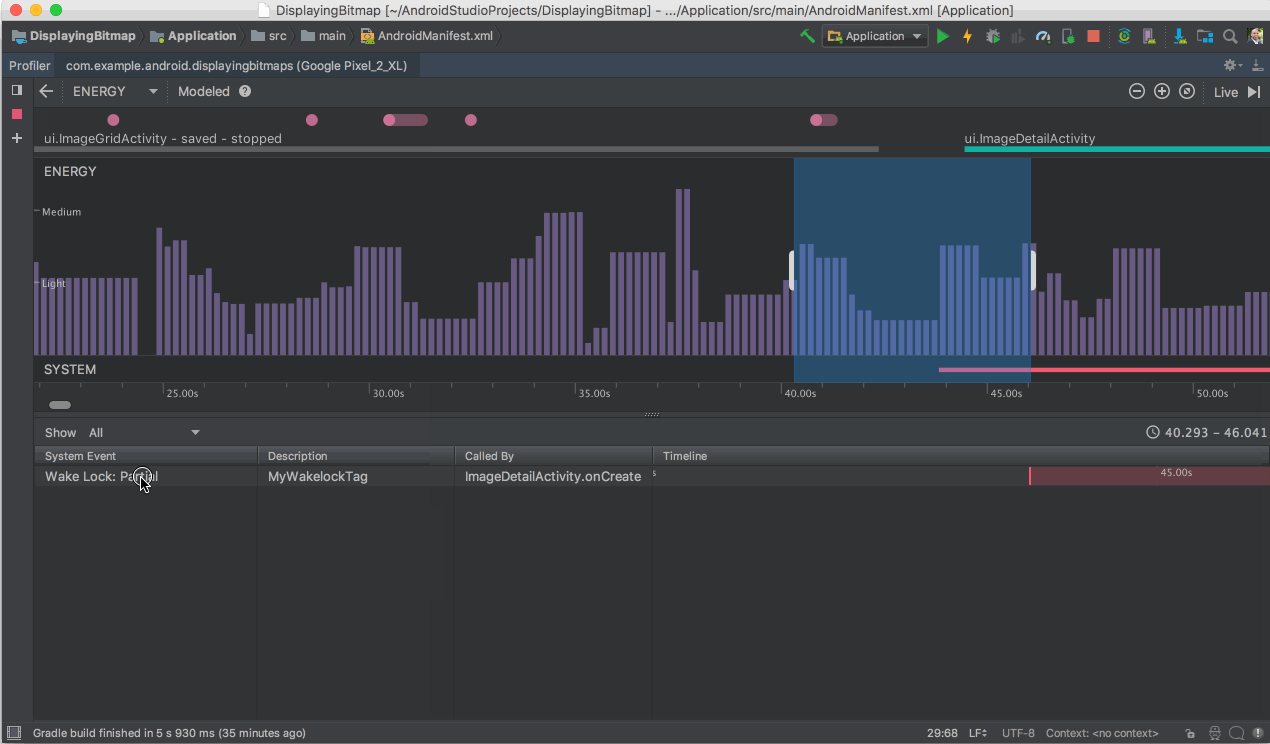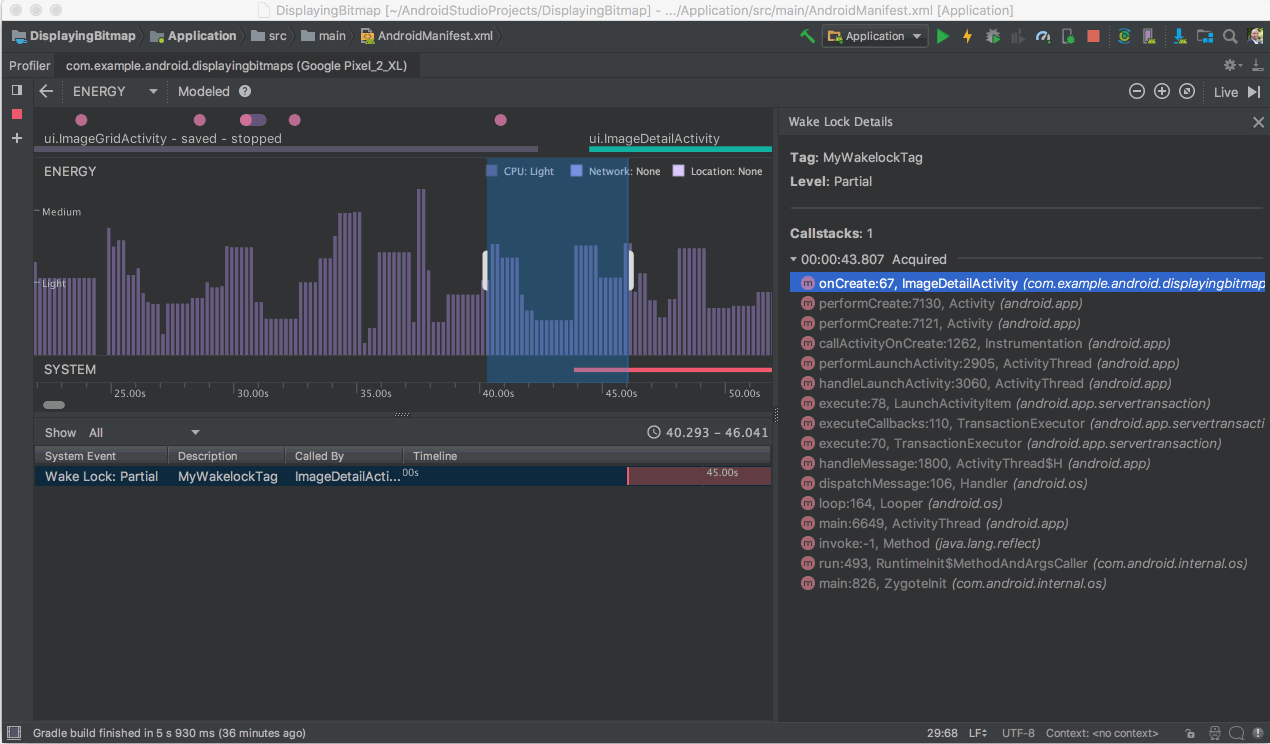
Another feature you do not want to miss is the Energy Profiler. This new profiler gives you a set of tools that will help you diagnose and improve the energy impact of your app. Better device battery life is one of the top most user requests, and with the Energy Profiler in Android Studio 3.2, you can do your part in improving device battery life by making sure your app is using the right amount of energy at the right time.
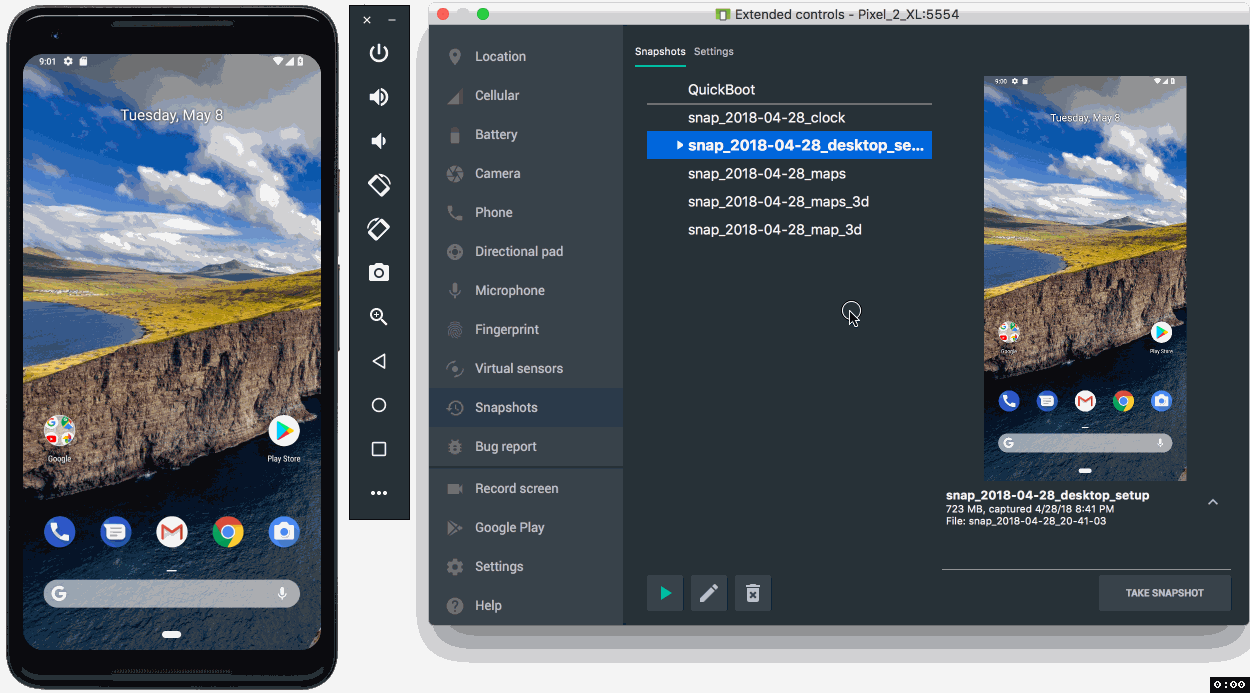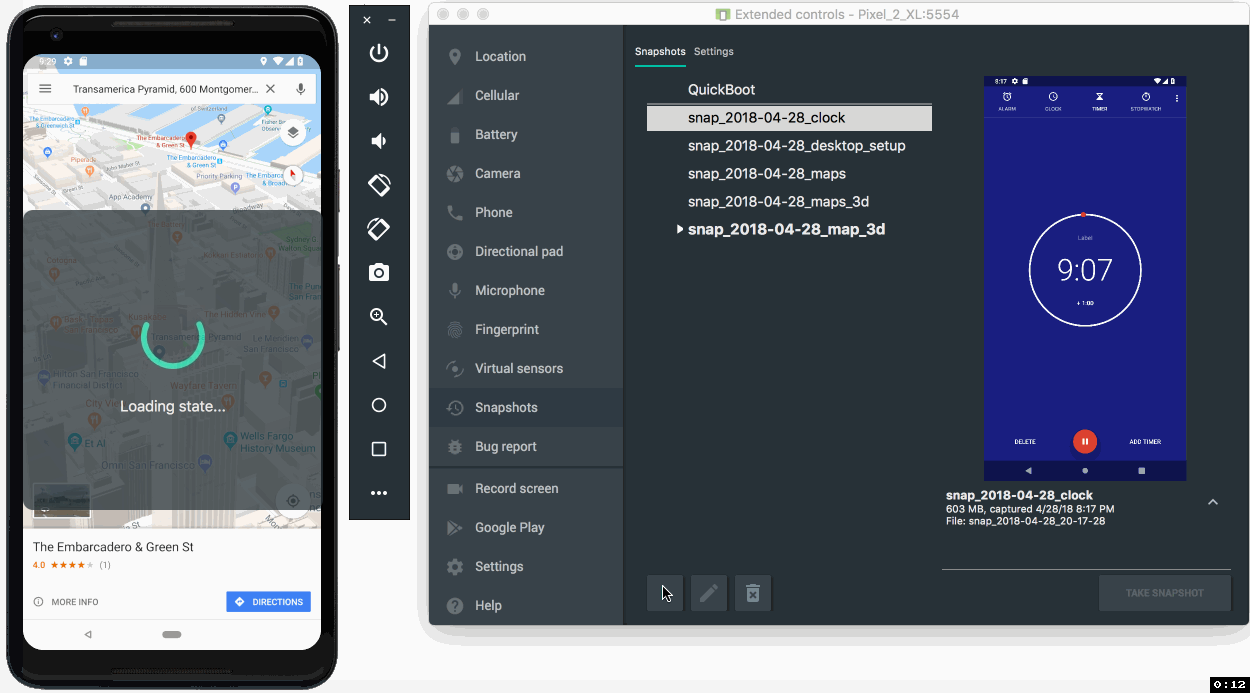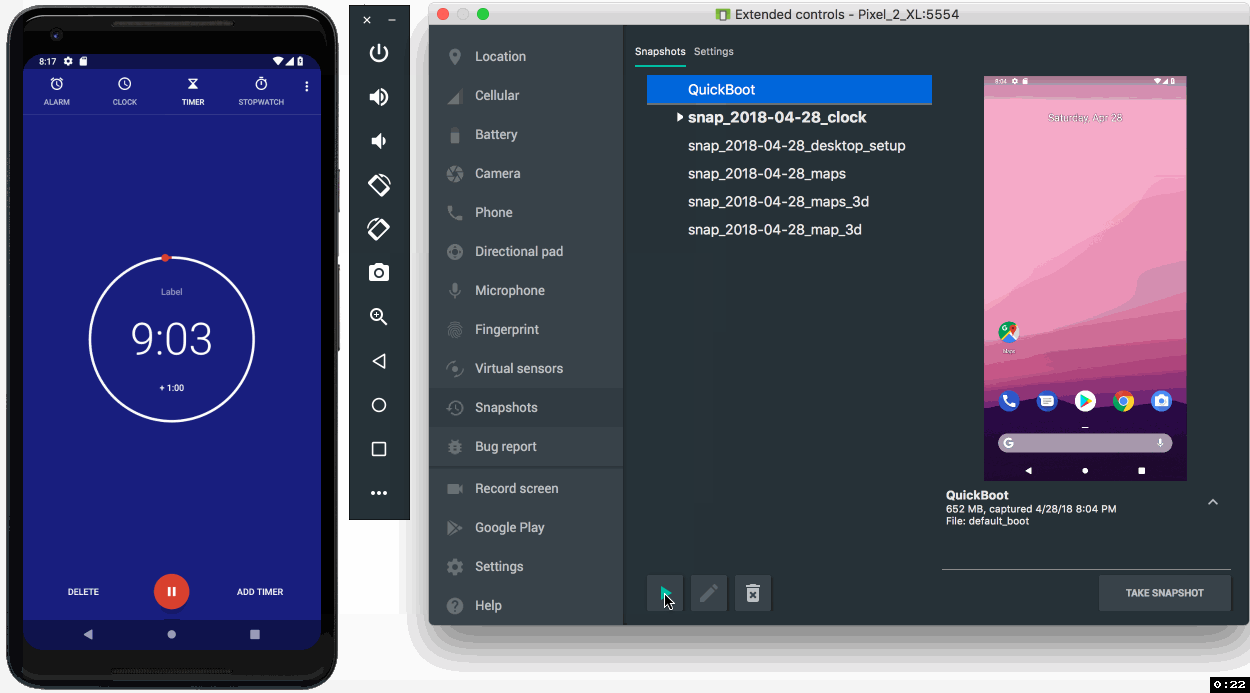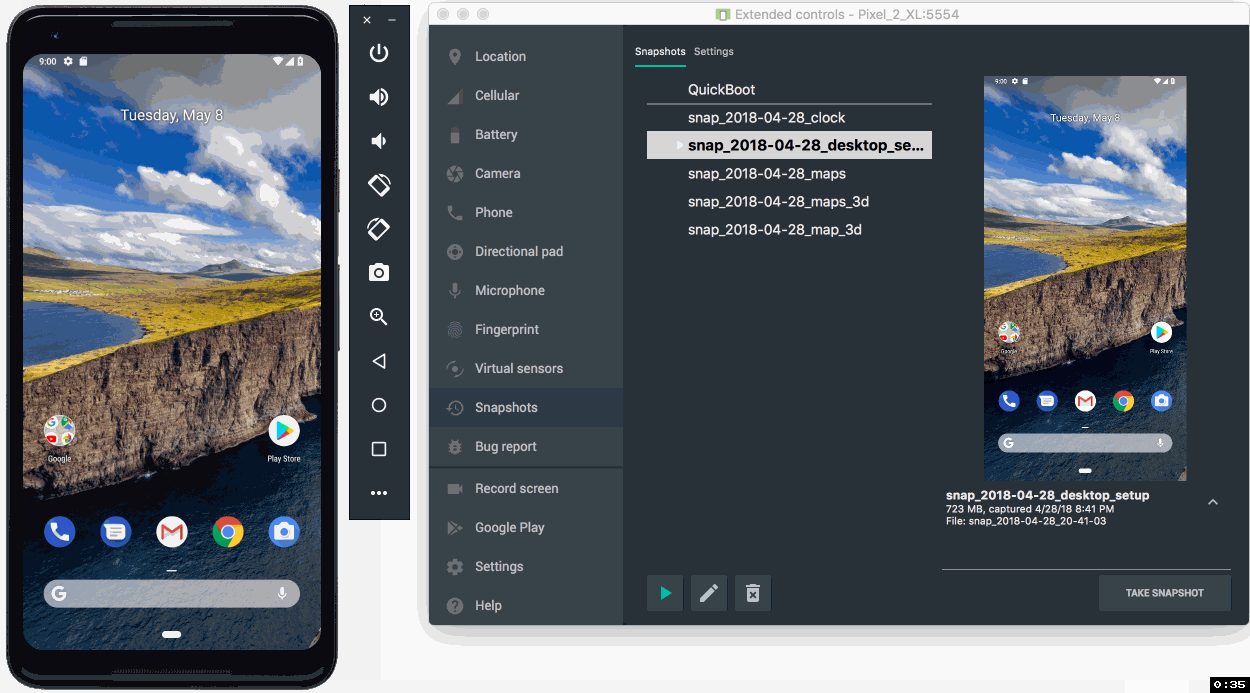
Lastly, you should also check out the new Android Emulator Snapshots feature. By using this feature, you can quickly take a snapshot of the current state of your emulator which includes the current state of the screen, apps, and settings. You can resume or boot into your emulator snapshot in under 2 seconds. For any app developer looking for super- fast boot times, or seeking to run tests in a predictable Android environment, Android Emulator Snapshots is a game changing feature for app development
On top of these major features, there are 20 new features plus many under-the-hood quality refinements in Android Studio 3.2. By using Android Studio 3.2, you can also develop for the latest technologies ranging from Android Jetpack, to the latest in Google Artificial Intelligence (AI) APIs with Android Slices.
Thank you to those who gave your early feedback on both the canary and beta releases. Your feedback helped us improve the quality and features in Android Studio 3.2. If you are ready for the next stable release, and want to use a new set of productivity features, Android Studio 3.2 is ready to download for you to get started.
Below is a full list of new features in Android Studio 3.2, organized by key developer flows.
Develop
- Slices support - Slices is a new way to tap into the built-in Android AI capabilities by surfacing app content in Google Search suggestions and the Google Assistant. Android Studio 3.2 has a built-in template to help you extend your app with the new Slice Provider APIs as well as new lint checks to ensure that you're following best practices when constructing the slices. To use, right-click on a project folder, and navigate to New→ Other→ Slice Provider. Learn more.
Slices Provider Template
- Sample Data - This feature allows you to use placeholder data to aid in the design of your app. This will help you visualize layouts that depend on runtime data. You can add built-in sample data to populate views such as RecyclerViews, ImageViews, and TextViews via a popup-window in the Layout Editor. Learn more.
- Material Design Update - When you start migrating from the Android Design support library to the new MaterialComponents app theme and library, Android Studio 3.2 will offer you access to new and updated widgets such as BottomAppBar, buttons, cards, text fields, new font styles and more. Learn more.
- CMakeList Editing Support - For those using C/C++ in their app, Android Studio has better support for CMake. With this release of Android Studio 3.2, code completion and syntax highlighting now works on common CMakeList build script commands.
- What's New Assistant - Android Studio 3.2 has a new assistant panel that opens automatically after an update to inform you about the latest changes to the IDE. You can also open the panel by navigating to Help → What's New in Android Studio.
- AndroidX Refactoring Support - One of the components of Android Jetpack is the introduction of the Android extension libraries (AndroidX) as a replacement for the Android Support Libraries. To add AndroidX to a new project you just need to add
android.useAndroidX=trueto yourgradle.propertiesfile. Additionally, Android Studio 3.2 has a new built-in refactoring action to help migrate your project the new namespace and dependencies. Also if you have any Maven dependencies that have not migrated to the AndroidX namespace, the Android Studio build system will automatically convert those project dependencies as well. Learn more.
- IntelliJ Platform Update - Android Studio 3.2 includes the IntelliJ 2018.1.6 platform release. This IntelliJ release adds many improvements to dataflow analysis, debugging, new inspections, inline external annotations, partial Git commits, plus much more. Learn more.
- Kotlin Update - Android Studio 3.2 bundles Kotlin 1.2.61, with support for the Kotlin-friendly Android 9 Pie SDK. Learn more.
Build
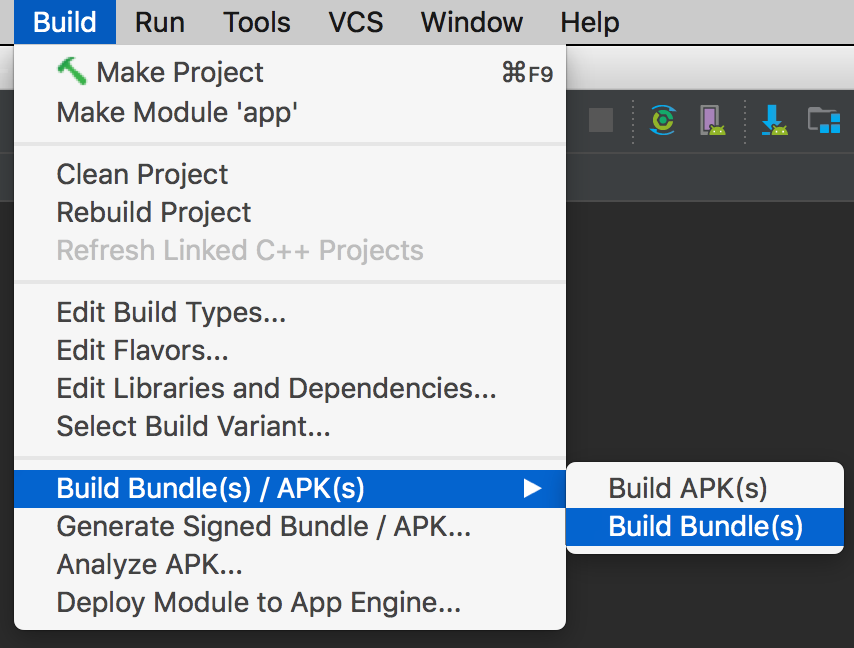
- Android App Bundle - The Android App Bundle is the new app publishing format designed to help you deliver smaller APKs to your users and reduce download size of your app. Google Play's new app serving model, called Dynamic Delivery, processes your app bundle to generate and serve optimized APKs for each user's device configuration, so they download only the code and resources they need to run your app. With Android Studio 3.2 or via the command line, you can easily build your code as an app bundle and get the benefit of smaller APKs based on language, screen density, and ABIs with no changes to your app code. Learn more.
Build Android App Bundle
- D8 Desugaring - In some cases, new Java Language features require new bytecodes and language APIs. However, older Android devices may not support these features. Desugaring allows you to use these features on older devices by replacing new bytecodes and language APIs with older ones during the build process. D8 desugaring is turned on by default for Android Studio 3.2 and you can now use most of the latest language changes while targeting older devices.
- R8 Optimizer - Starting with Android Studio 3.2, we are starting the transition to use R8 as a replacement for ProGuard to optimize and shrink Java language bytecode. R8 is still experimental, so we do not recommend publishing your app using R8 yet, but it is a good time to give the Android Studio team early feedback so we can make any adjustments before R8 fully replaces ProGuard. Learn more.
Test
- Emulator Snapshots - The latest release of the Android Emulator allows you to create a snapshot of the current state of your emulator and boot up and switch into any snapshot in under 2 seconds. Built upon the Android Emulator Quickboot feature, Android Snapshots are even faster to save and load with this stable release due to under-the-hood speed enhancements. When testing and developing your app, Android snapshots allow you to pre-configure an Android Virtual Device (AVD) snapshot with the presets, apps, data and settings that you want in-place, and repeatedly go back to the same snapshot. Learn more.
Android Emulator Snapshots
- Microsoft® Hyper-V™ Support - You can now run the Android Emulator on Windows® 10 computers that have Hyper-V enabled. Intel HAXM is still the default hypervisor for the fastest Android Emulator experience. However,thanks to recent open source contributions by Microsoft, and the addition of the new Windows Hypervisor Platform (WHPX) API, the Android Emulator can coexist with other Hyper-V-backed applications, like local Virtual Machines, using the new Hyper-V Support. Learn more.
- AMD® Processor Support - AMD Processors are now supported by the Android Emulator on Windows 10. Previously running the Android Emulator was limited to slow software emulation when running Windows, but developers who have an AMD processor can now have hardware accelerated performance. Learn more.
- Screen Record in Android Emulator - You can now record both screen and audio on any Android API level with the new screen record feature in the Android Emulator. In the past, screen recording on a physical Android device only worked on Android 4.4 KitKat (API 19) and above with no audio, with limited Android Emulator support. With the latest Android Emulator (v28.0.+) you no longer have this restriction. As an added bonus, there is a built-in conversion to output to GIF and WebM. You can trigger the new screen record feature via the Android Emulator Extended Controls panel, command line and from Android Studio. Lean more
- Virtual Scene Camera for Android Emulator - The new Virtual Scene camera in the Android Emulator helps you to develop for ARCore, Google's platform for building augmented reality experiences. The emulator is calibrated to work with ARCore APIs for AR apps and also allows you to inject virtual scene bitmap images. The virtual scene camera can also be used as a regular HAL3 compatible camera. Learn more.
- ADB Connection Assistant - Android Studio 3.2 has a new assistant system to help troubleshoot your Android ADB device connections issues. The ADB Connection Assistant walks you through common troubleshooting steps to connect your Android device to your development machine. You can trigger the assistant from the Run dialog box or by navigating to Tools → Connection Assistant . Learn more.
Optimize
- Energy Profiler - Battery life is a key concern for many phone users, and your app may impact battery life more than you realize. The new Energy Profiler in the Android Studio performance profiler suite can help you understand the energy impact of your app on an Android device. You can now visualize the estimated energy usage of system components, plus inspect background events that may contribute to battery drain. To use the energy profiler, ensure you are connected to an Android device or emulator running Android 8.0 Oreo (API 26) or higher. Learn more.
Energy Profiler
- System Trace - The new System Trace feature in the CPU Profiler allows you to inspect how your app interacts with system resources in fine-grained detail. Inspect exact timings and durations of your thread states, visualize where your CPU bottlenecks are across all cores, and add custom trace events to analyze. To use system trace, start profiling your app, click into the CPU Profiler, and then choose the System Trace recording configuration. Learn more.
- Profiler Sessions - We now automatically save Profiler data as "sessions" to revisit and inspect later while you have Android Studio open. We've also added the ability to import and export your CPU recordings and heap dumps for later analysis or inspection with other tools. Learn more.
- Automatic CPU Recording - You can now automatically record CPU activity using the Debug API. After you deploy your app to a device, the profiler automatically starts recording CPU activity when your app calls
startMethodTracing(String tracePath), and stops recording when your app callsstopMethodTracing(). Similarly, you can also now automatically start recording CPU activity on app start-up by enabling Start Recording a Method Trace on Startup option in your run configuration. Learn more.
- JNI Reference Tracking - For those of you who have C/C++ code in your Android app, Android Studio 3.2 now allows you to inspect the memory allocations of your JNI code in the Memory Profiler. As long as you deploy your app to a device running Android 8.0 Oreo (API 26) and higher, you can drill down into the allocation call stack from your JNI reference. To use the feature, start a memory profiler session, and select the JNI Heap from the Live Allocation drop-down menu. Learn more.
To recap, the latest canary of Android Studio 3.2 includes these new major features:
Develop
Build
|
Test
Optimize
|
Check out the release notes for more details.
Getting Started
Download the latest version of Android Studio 3.2 from the download page. If you are using a previous canary release of Android Studio, make sure you update to Android Studio Canary 14 or higher. If you want to maintain a stable version of Android Studio, you can run the stable release version and canary release versions of Android Studio at the same time. Learn more.
To use the mentioned Android Emulator features make sure you are running at least Android Emulator v28.0.7+ downloaded via the Android Studio SDK Manager.
We appreciate any feedback on things you like, and issues or features you would like to see. Please note, to maintain high product quality, a couple features (e.g. Navigation Editor) you saw in earlier release channels are not enabled by default in the stable release channel. If you find a bug or issue, feel free to file an issue. Connect with us -- the Android Studio development team ‐ on our Google+ page or on Twitter.








 Posted by Nevin Mital, Partner Developer Relations
Posted by Nevin Mital, Partner Developer Relations

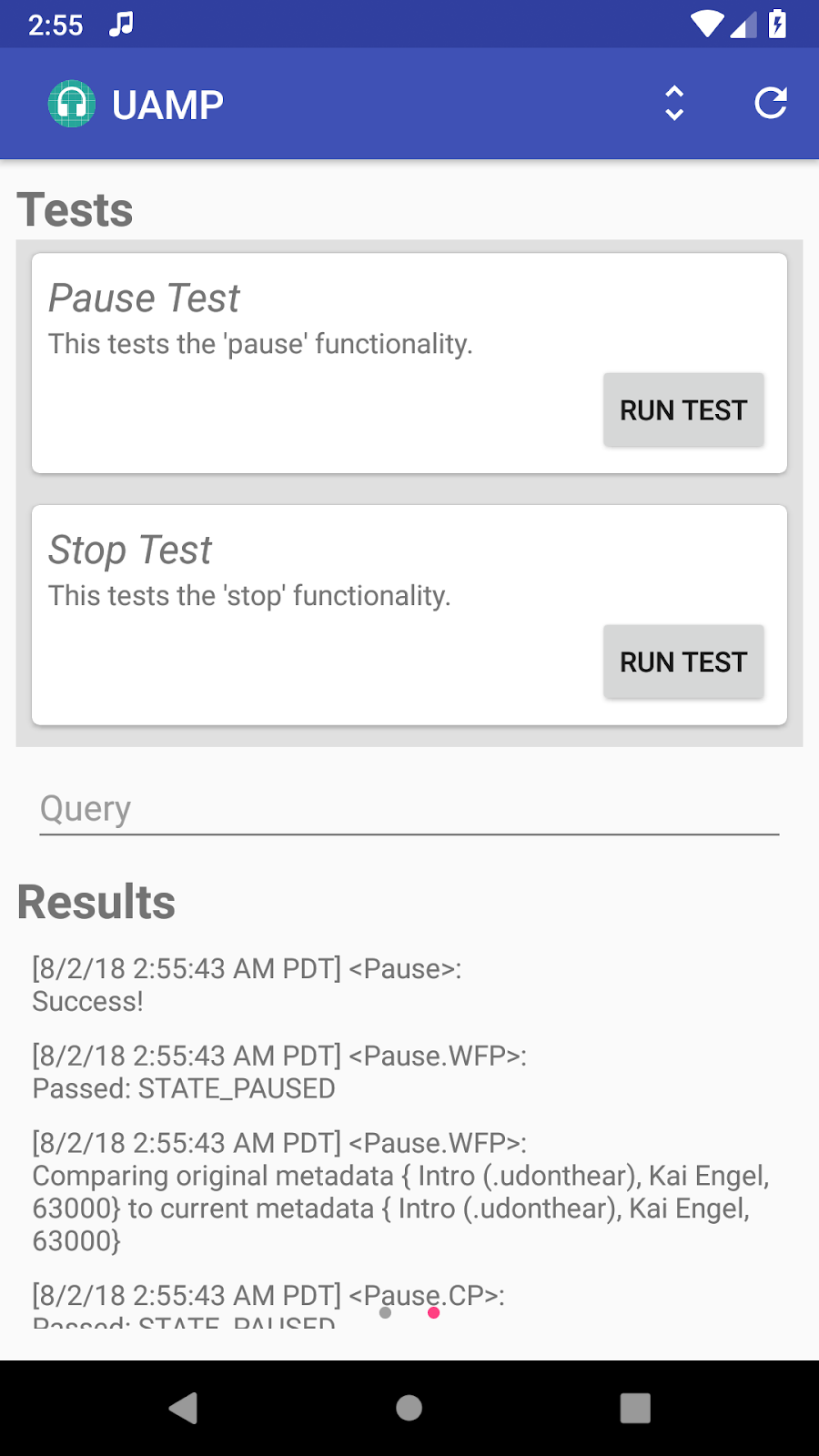

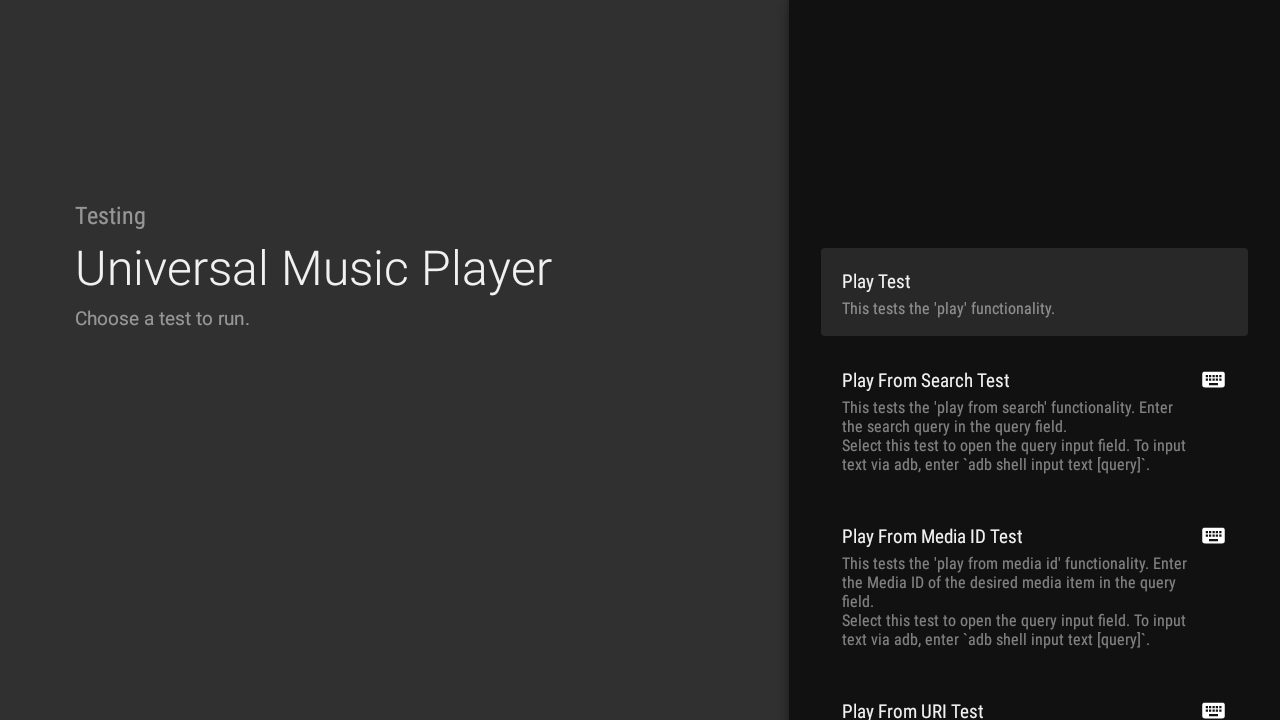
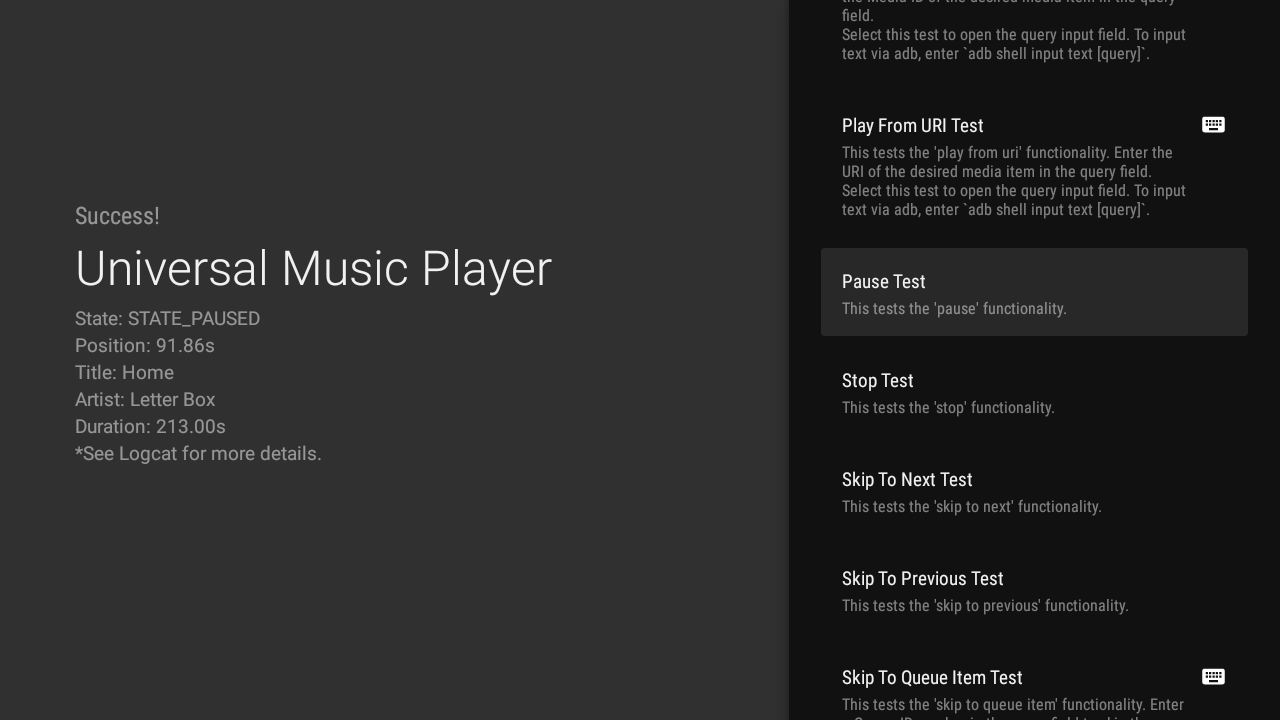
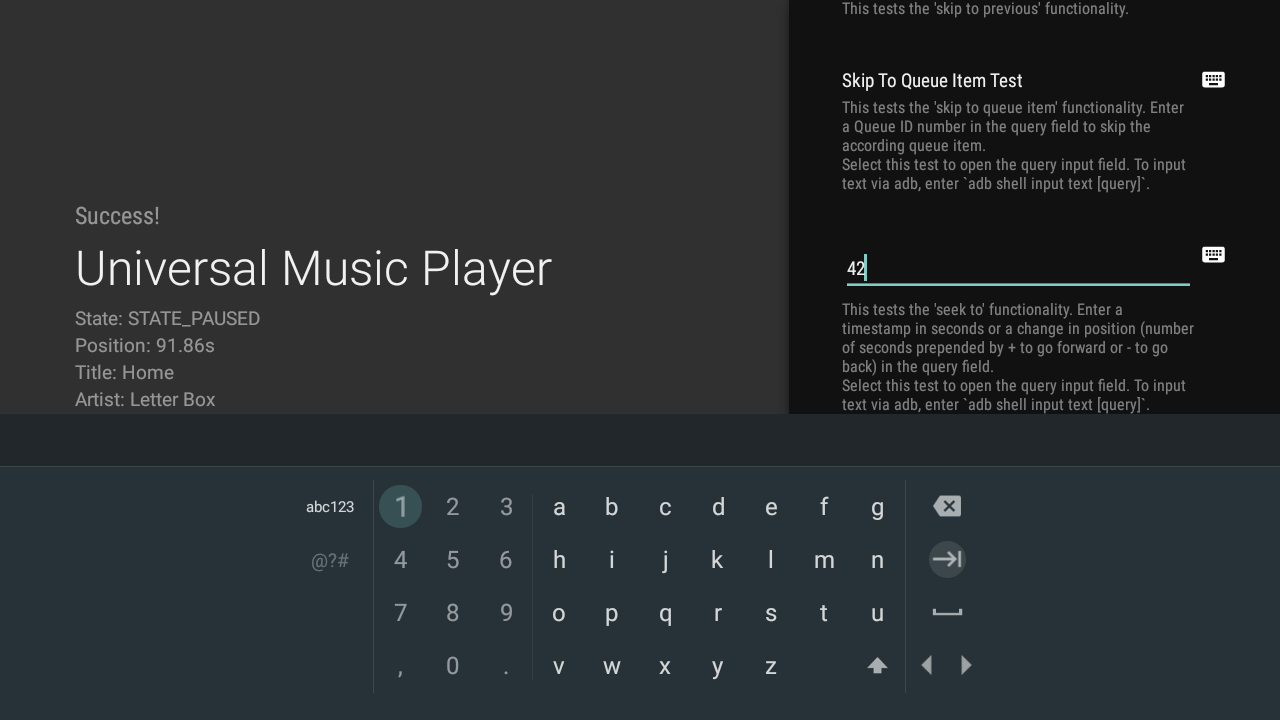

 Posted by Vlad Zavidovych, Software Engineer; Artem Yudin, Software Engineer
Posted by Vlad Zavidovych, Software Engineer; Artem Yudin, Software Engineer

