Posted By Dave Burke, VP of Engineering
Four weeks ago at Google I/O we released the first beta version of Android P, putting AI at the core of the operating system and focusing on intelligent and simple experiences.
We talked about some of Android's newest features in the keynotes and went deep on the developer APIs during the breakouts. If you missed the livestream, make sure to check out the full playlist of Android talks.
Today we're releasing Android P Beta 2, an update that includes the final Android P APIs, the latest system images, and updated developer tools to help you get ready for the consumer release coming later in the summer.
You can get Android P Beta 2 on Pixel devices by enrolling here. If you're already enrolled and received the Android P Beta 1 on your Pixel device, you'll automatically get the update to Beta 2. Partners that are participating in the Android P Beta program will be updating their devices over the coming weeks.
Enhance your app with Android P features and APIs
Android P Beta 2 is the latest update of our upcoming Android P platform and includes the final APIs (API level 28) as well as the official SDK. You can get started building with the Android P features and APIs today. Here are a few we want you to try -- head over to the features overview for more.
Machine learning at the core
We partnered with DeepMind on a feature we call Adaptive Battery that uses machine learning to prioritize system resources for the apps the user cares about most. If your app is optimized for Doze, App Standby, and Background Limits, Adaptive Battery should work well for you right out of the box. Make sure to check out the details in the power documentation to see how it works and where the impacts could be, and test your apps to make sure they are ready.
App Actions is a new way to help you raise the visibility of your app and help drive engagement. Actions take advantage of machine learning on Android to surface your app to the user at just the right time, based on your app's semantic intents and the user's context. Actions work on Android P and earlier versions of the platform and they'll be available soon for you to start using. Sign up here to be notified when Actions are available.
Slices are a new way to surface rich, templated content in places like Google Search and Assistant. They're interactive, and through Android Jetpack they're compatible all the way back to KitKat. Check out the Getting Started guide to learn how to build with Slices -- you can use the SliceViewer tool to see how your Slices look. Over time we plan to expand the number of places that your Slices can appear, including remote display in other apps.
Simplicity, polish
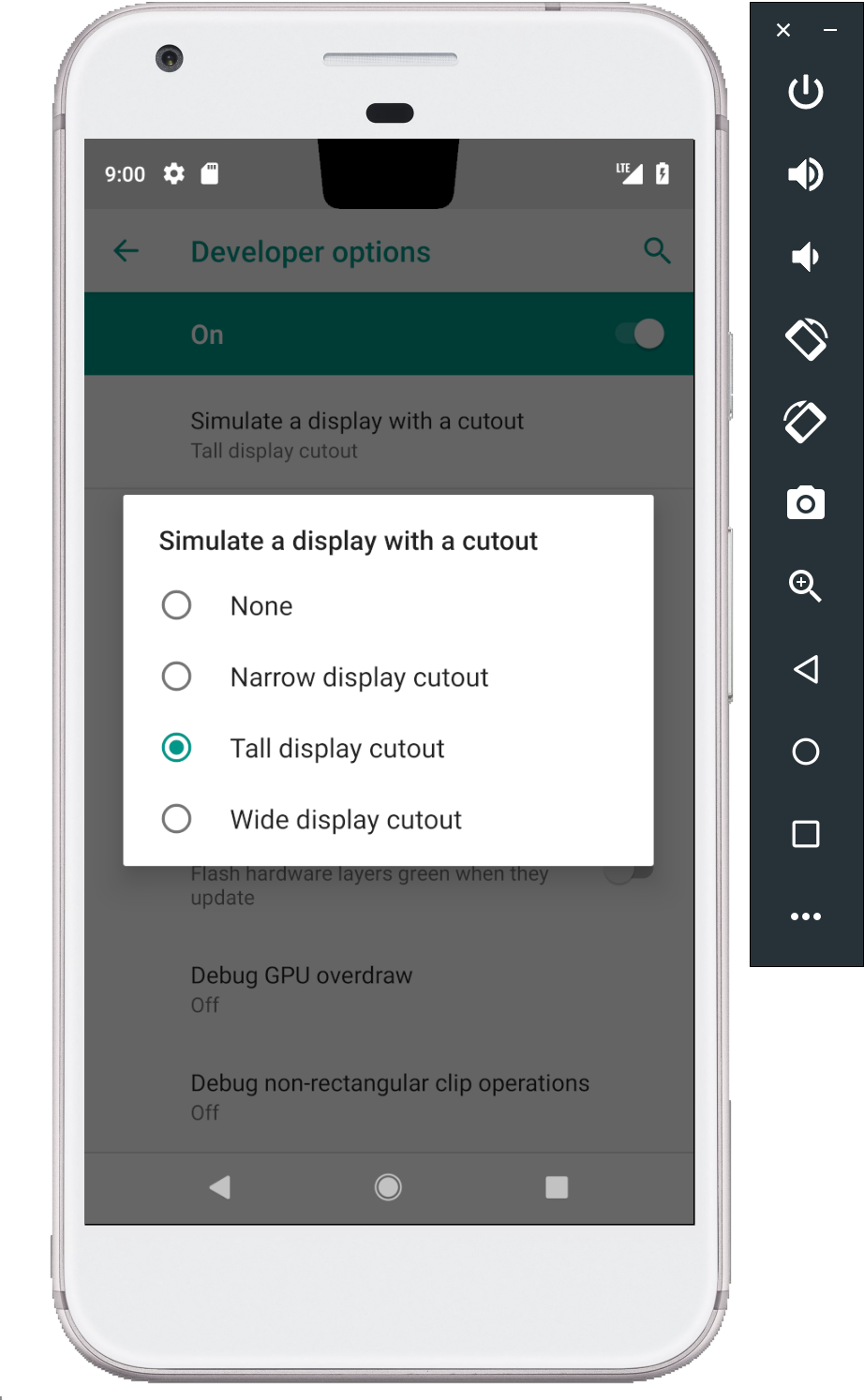
Android P adds platform support for screens with display cutouts, and we've added new APIs to let you deliver a rich, edge-to-edge experience on the latest screens. Cutout support works seamlessly for apps, with the system managing status bar height to separate your content from the cutout. If you have immersive content, you can use the display cutout APIs to check the position and shape of the cutout and request full-screen layout around it.
All developers should check out the docs to learn how to manage the cutout area and avoid common compatibility issues that can affect apps. Make sure to test your app on a device that has a display cutout, such as one of the Android P Beta devices.
Apps with immersive content can display content fullscreen on devices with a display cutout.
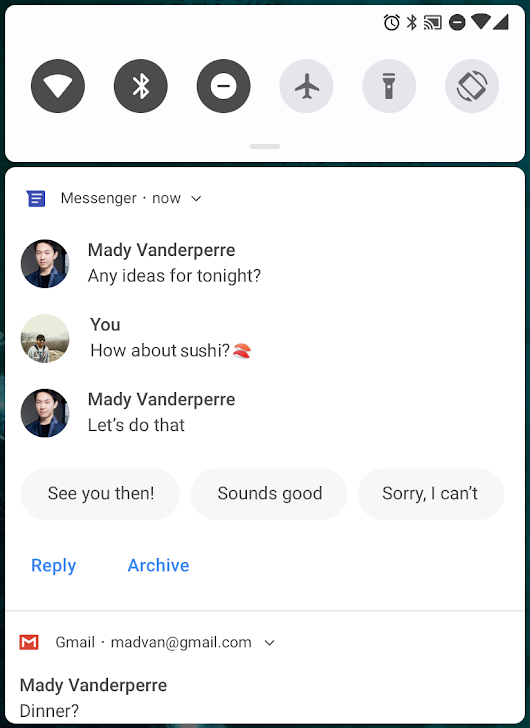
If your app uses messaging notifications, take advantage of the changes in MessagingStyle that make notifications even more useful and actionable. You can now show conversations, attach photos and stickers, and even suggest smart replies. You'll soon be able to use ML Kit to generate smart reply suggestions your app.
MessagingStyle notifications with conversations and smart replies [left], images and stickers [right].
Security
With a range of biometric sensors in use for authentication, we've made the experience more consistent across sensor types and apps. Android P introduces a system-managed dialog to prompt the user for any supported type of biometric authentication. Apps no longer need to build their own dialog -- instead they use the BiometricPrompt API to show the standard system dialog. In addition to Fingerprint (including in-display sensors), the API supports Face and Iris authentication.
If your app is drawing its own fingerprint auth dialogs, you should switch to using the BiometricPrompt API as soon as possible.
More
If your app uses the device camera, try the new multi-camera APIs that let you access streams simultaneously from two or more physical cameras. On devices with dual cameras, you can create innovative features not possible with a single camera -- such as seamless zoom, bokeh, and stereo vision. You can get started today using any of the Android P Beta devices that offers a dual camera.
Audio apps can use the Dynamics Processing API for access to a multi-stage, multi-band dynamics processing effect to modify the audio coming out of Android devices and optimize it according to the preferences of the listener or the ambient conditions.
 Take a look at the Android P features overview for a complete list of the new features and APIs.
Take a look at the Android P features overview for a complete list of the new features and APIs.
Get started in a few simple steps
First, make your app compatible and give your users a seamless transition to Android P. Just install your current app from Google Play on a Android P Beta device or emulator and test -- the app should run and look great, and handle Android P behavior change for all apps properly. After you've made any necessary updates, we recommend publishing to Google Play right away without changing the app's platform targeting.
If you don't have a supported device, remember that you can set up an Android Virtual Device on the Android Emulator as your test environment instead. If you haven't tried the emulator recently, you'll find that it's incredibly fast, boots in under 6 seconds, and even lets you model next-gen screens -- such as long screens and screens with display cutout.
Next, update your app's targetSdkVersion to 28 as soon as possible, so Android P users of your app can benefit from the platform's latest security, performance, and stability features. If your app is already targeting API 26+ in line with Google Play's upcoming policies, then changing to target 28 should be a small jump.
It's also important to test your apps for uses of non-SDK interfaces and reduce your reliance on them. As noted previously, in Android P we're starting a gradual process to restrict access to selected non-SDK interfaces. Watch for logcat warnings that highlight direct uses of restricted non-SDK interfaces and try the new StrictMode method detectNonSdkApiUsage() to catch accesses programmatically. Where possible, you should move to using public equivalents from the Android SDK or NDK. If there's no public API that meets your use-case, please let us know.
When you're ready, dive into Android P and learn about the new features and APIs to extend your apps. To build with the new APIs, just download the official API 28 SDK and tools into Android Studio 3.1, or use the latest version of Android Studio 3.2. Then update your project's compileSdkVersion and targetSdkVersion to API 28.
Visit the Developer Preview site for details and documentation. Also check out this video and the Google I/O Android playlist for more on what's new in Android P for developers.
Publish to Google Play alpha, beta, or production channels
Starting today you can publish your APK updates that are compiled against, or optionally targeting, API 28. Publishing an update to Google Play during the preview lets you push updates to users to test compatibility on existing devices, including devices running Android P Beta 2.
To make sure that your updated app runs well on Android P as well as older versions, a common strategy is to use Google Play's beta testing feature to get early feedback from a small group of users -- including Android P Beta 2 users — and then do a staged rollout to production.
How to get Android P Beta 2
For Pixel devices, you can enroll your device in the Android Beta program and you'll automatically receive the update to Android P Beta 2 over-the-air. If you're already enrolled and received Beta 1, watch for the update coming your way soon. Partners that are participating in the Android P Beta program will be updating their devices over the coming weeks.
You can see the full list of supported partner and Pixel devices at android.com/beta. For each device you'll find specs and links to the manufacturer's dedicated site for downloads, support, and to report issues.
Thanks for all of your feedback so far. Please continue to share feedback or requests as we work towards the consumer release later this summer. Feel free to use our hotlists for platform issues, app compatibility issues, and third-party SDK issues.
We're looking forward to seeing your apps on Android P!