Posted by Dave Burke, VP of Engineering

Android has led the way towards the future of mobile, with new technologies like 5G to foldable displays to machine learning built into the core. A hallmark of our approach is a strong developer community that provides early and thoughtful feedback, helping us deliver a robust platform for apps and games that delight billions of users around the world. So today, we’re releasing the first Developer Preview of Android 11, and building on a strong feedback cycle last year, we’re making this year’s preview available to you earlier than ever.
With Android 11 we’re keeping our focus on helping users take advantage of the latest innovations, while continuing to keep privacy and security a top priority. We’ve added multiple new features to help users manage access to sensitive data and files, and we’ve hardened critical areas of the platform to keep the OS resilient and secure. For developers, Android 11 has a ton of new capabilities for your apps, like enhancements for foldables and 5G, call-screening APIs, new media and camera capabilities, machine learning, and more.
This is just a first look; like prior years, we’ll continue to share new features and updates over the coming months and into Google I/O as we work through your feedback. The most important thing for you to do right now is this: visit the Android 11 developer site, download a system image for your Pixel 2, 3, 3a, or 4 device, and let us know what you think!
Today’s release is an early baseline build for developers only and not intended for daily or consumer use, so we're making it available by manual download and flash only. Remember, getting early input from you is crucial in helping us evolve the platform to meet your needs. Read on for a taste of what’s new in Android 11, and visit the developer site for details on timeline, how to test, and how to give feedback.
Helpful innovation
5G experiences
5G brings consistently faster speeds and lower latency to more users around the world. With 5G you can extend your Wi-Fi app experiences -- such as streaming 4K video or loading higher-res game assets -- to mobile users, or you can build new experiences designed specifically for 5G. In Android 11 we’re enhancing and updating the existing connectivity APIs so you can take advantage of 5G’s improved speeds.
- Dynamic meteredness API - with this API you can check whether the connection is unmetered, and if so, offer higher resolution or quality that may use more data. We’ve extended the API to include cellular networks, so that you can identify users whose carriers are offering truly unmetered data while connected to the carrier’s 5G network.
- Bandwidth estimator API - we’ve updated this API for 5G to make it easier to check the downstream/upstream bandwidth, without needing to poll the network or compute your own estimate. If the modem doesn’t provide support, we make a default estimation based on the current connection.
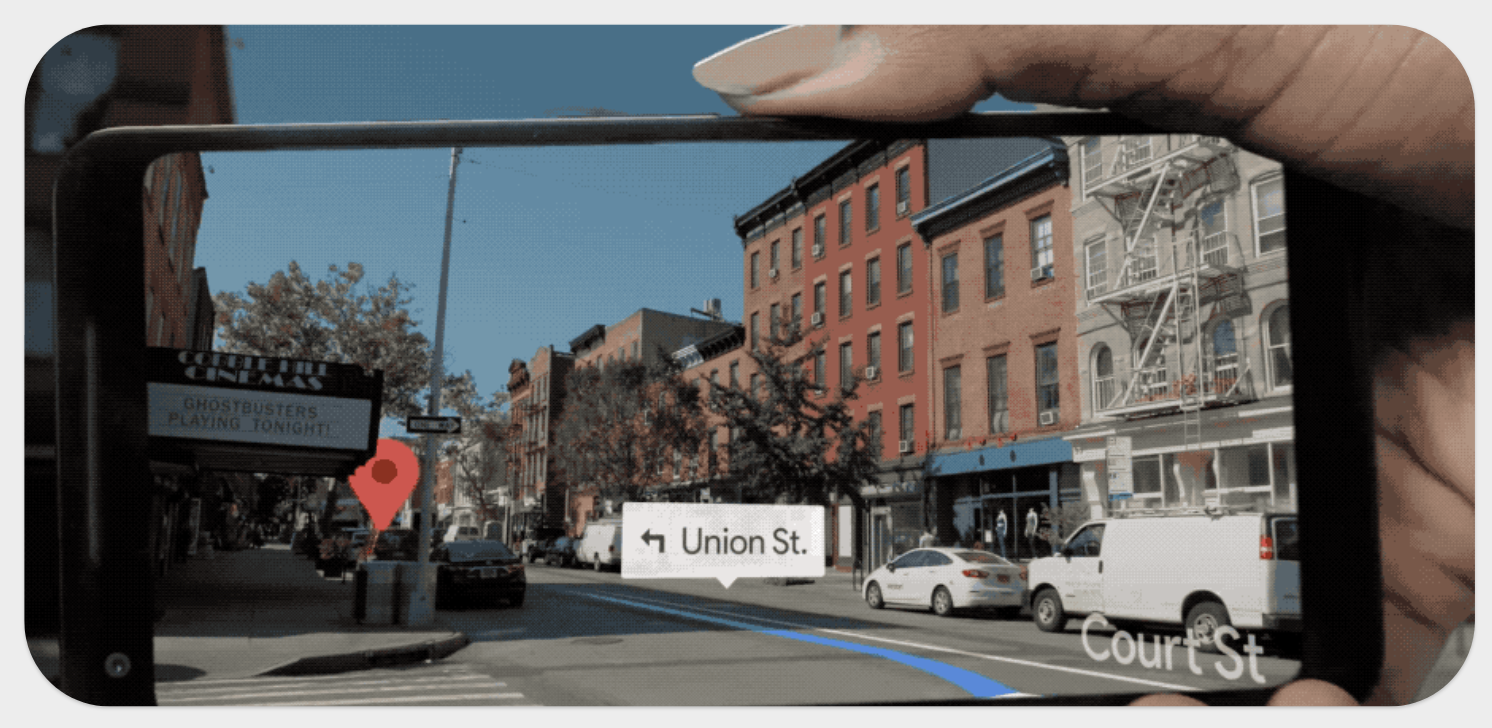
Moving beyond the home, 5G can for example let you enhance your “on-the-go” experience by providing seamless interactions with the world around you from friends and family to businesses.
New screen types
Device makers are continuing to innovate by bringing exciting new form-factors and device screens to market. We’ve extended support for these in the platform, with APIs to let you optimize your apps.
- Pinhole and waterfall screens - Apps can manage pinhole screens and waterfall screens using the existing display cutout APIs. If you want, a new API lets your app use the entire waterfall screen including the edges, with insets to help you manage interaction near the edges.
People and conversations
Communicating with your friends and colleagues is the most important thing many people do on their phones. In Android 11, we are introducing changes that help developers create deeper conversational experiences, a few of which you’ll see early versions of in DP1:
- Dedicated conversations section in the notification shade - users can instantly find their ongoing conversations with people in their favorite apps.
- Bubbles - Bubbles are a way to keep conversations in view and accessible while multi-tasking on their phones. Messaging and chat apps should use the Bubbles API on notifications to enable this in Android 11.
- Insert images into notification replies - if your app supports image copy/paste, you can now let users insert assets directly into notification inline replies to enable richer communication as well as in the app itself. As part of DP1 - you’ll see image copy support in Chrome and image paste support via Gboard clipboard.
Real-time, bilateral communication apps should use the sharing/conversation shortcuts API to provide
People targets that Android will surface throughout the phone as well as
Bubble APIs to allow users to carry on conversations while using the device in other capacities.
Neural Networks API 1.3
Neural Networks API (NNAPI) is designed for running computationally intensive operations for machine learning on Android devices. In Android 11, we’re expanding the operations and controls available to developers. In this release, we’ve added new operations and execution controls to help optimize common use cases:
- Quality of Service APIs support priority and timeout for model execution.
- Memory Domain APIs reduce memory copying and transformation for consecutive model execution.
- Expanded quantization support, we’ve added signed integer asymmetric quantization where signed integers are used in place of float numbers to enable smaller models and faster inference.
See the NDK sample code for examples using these new APIs.
Watch for more coming in later preview updates. We’re working with hardware vendors and popular machine learning frameworks such as TensorFlow to optimize and roll out support for NNAPI 1.3.
Privacy and security
Privacy
Privacy has always been at the core of Android, and each year we’ve added more ways to keep users secure and increase transparency and control. These changes have been popular with users - for example in Android 10 we added the “While app is in use” permission option to give users more granular control over their location and limit background location access. So far, when given the “While app is in use” option, about half of users select it.
In Android 11 we’re continuing our focus on user privacy with new permission options, updates to scoped storage, and more. Please give these features a try with your apps right away and let us know what you think.
- One-time permission - For the most sensitive types of data - not just location but also for the device microphone and camera - users can now grant temporary access through a one-time permission. This permission means that apps can access the data until the user moves away from the app, and they must then request permission again for the next access. More information here.

One-time permission dialog in Android 11.
- Scoped storage - We’ve continued our work to better protect app and user data on external storage, and made further improvements to help developers migrate more easily. We want to take a moment to acknowledge everyone in the Android community who gave us such helpful feedback - thank you so much for helping us make the platform better! This preview release includes several enhancements, such as opt-in raw file path access for media, updated DocumentsUI, and batch edit operations in MediaStore. Along with these technical changes, based on your input, we are also giving you more time to make the migration and the changes will apply to your apps when they target Android 11. Read more here and watch for more enhancements in subsequent updates.
In addition to these platform changes, users tell us that they want more protection on earlier versions of Android and more transparency around how apps will use this data, so we are updating Google Play Policy to ensure that apps only request location permissions when truly necessary. Read more
Security
We focus on raising the bar for security with each version of Android -- from reaching more devices with monthly security updates to building more protections into the latest platform. In Android 11, we’ve extended Android’s defense-in-depth strategies to more areas of the platform and added new features and APIs for apps.
- Biometrics - We’ve expanded our biometrics support to meet the needs of a wider range of devices. BiometricPrompt now supports three authenticator types with different levels of granularity -- strong, weak, and device credential. We’ve also decoupled the BiometricPrompt flow from the app’s Activity lifecycle to make it easier to integrate with various app architectures, and to improve the transaction UI. All apps using biometric auth should move to the BiometricPrompt APIs, which are also available in AndroidX for compatibility with earlier versions of Android.
- Platform hardening - We’ve expanded use of compiler-based sanitizers in security-critical components, including BoundSan, IntSan, CFI, and Shadow-Call Stack. We’re also enabling heap pointer tagging for apps targeting Android 11 or higher, to help apps catch memory issues in production. These hardening improvements may surface more repeatable/reproducible app crashes in your code, so please test your apps. We've used HWAsan to find and fix many memory errors in the system, and we now offer HWAsan-enabled system images to help you find such issues in your apps.
- Secure storage and sharing of data - Apps can now share data blobs easily and more safely with other apps through a BlobstoreManager. The Blob store is ideal for use-cases like sharing ML models among multiple apps for the same user.
- Identity credentials - Android 11 adds platform support for secure storage and retrieval of verifiable identification documents, such as ISO 18013-5 compliant Mobile Driving Licenses. We’ll have more details to share on this soon!
Updates and compatibility
Google Play System Updates
Since Android 10, we’ve been scaling up our investment in Google Play System Updates (Project Mainline) to improve security, privacy, and consistency across the ecosystem. Thanks to strong collaboration with device makers, we’ve made significant progress towards this goal and have expanded our infrastructure to reach a wider range of devices more safely and quickly.
In Android 11, we’ve added 12 new updatable modules, for a total of 22 modules. Highlights include a permissions module that standardizes user and developer access to critical privacy controls on Android devices, a media provider module that’s integral to our privacy efforts around Scoped Storage, and an NNAPI (Neural Networks API) module that optimizes performance and guarantees consistent APIs across devices. To learn more about Google Play System Updates, check out the Project Mainline blog post.
App compatibility
We’re also working to make updates faster and smoother by prioritizing app compatibility as we roll out new platform versions. In Android 11 we’ve added new processes, developer tools, and release milestones to minimize the impact of platform updates.
- Minimizing the impact of behavior changes - While changes we make to Android can make the OS more helpful, secure, and better performing, some of these changes can affect developers’ apps. As we built Android 11, we made a conscious effort to minimize behavioral changes that could affect apps by closely reviewing their impact and by making them opt-in, wherever possible, until you set targetSdkVersion to 'R' in your app. We hope this gives developers more control, and leads to more apps working out-of-the-box on Android 11.
- Easier testing and debugging - To help you test for compatibility, we’ve made many of the breaking changes toggleable - meaning that you can force-enable or disable the changes individually from Developer options or adb. With this change, there’s no longer a need to change targetSdkVersion or recompile your app for basic testing. Check out the details here.
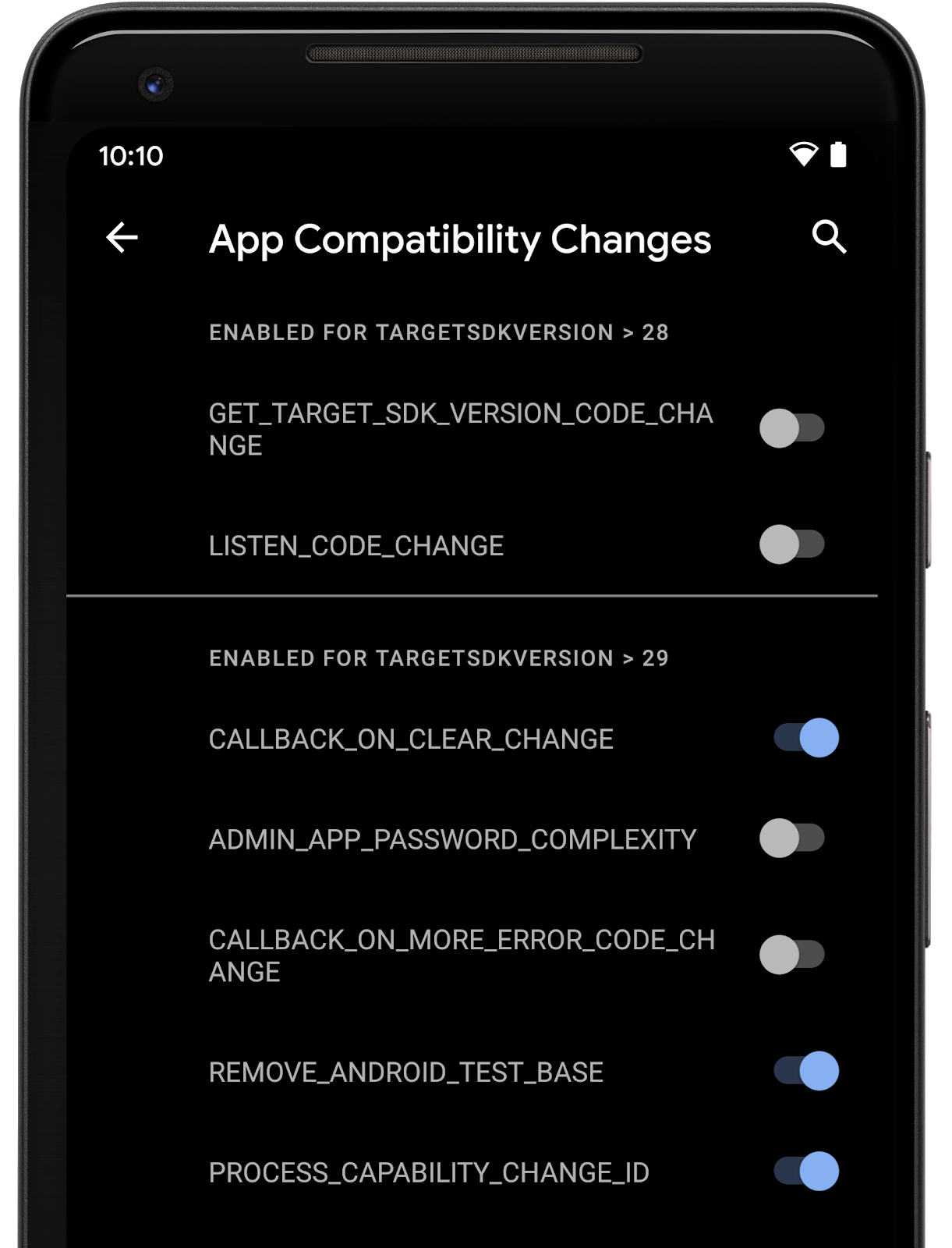
App compatibility toggles in Developer Options.
- Updated greylists - We’ve updated the lists of restricted non-SDK interfaces, and as always your feedback and requests for public API equivalents are welcome.
- Dynamic resource loader - As part of their migration away from non-SDK interfaces, developers asked us for a public API to load resources and assets dynamically at runtime. We’ve now added a Resource Loader framework in Android 11, and thank you to the developers who gave us this input!
- New platform stability milestone - Developers also told us that preparing for early app compatibility was a challenge without a clear date for final changes. So in Android 11 we’re adding a new release milestone called “Platform Stability”, which we expect to reach in early June. This milestone includes not only final SDK/NDK APIs, but also final internal APIs and system behaviors that may affect apps. We hope you can use this new milestone to plan your final development and testing. More on the release timeline is here.
Polish and quality
Connectivity
- Call screening service improvements - call-screening apps can now do more to help users. Apps can get the incoming call’s STIR/SHAKEN verification status as part of the call details, and they can customize a system-provided post call screen to let users perform actions such as marking a call as spam or adding to contacts.
- Wi-Fi suggestion API enhancements - We’ve extended the Wi-Fi suggestion API to give connectivity management apps greater ability to manage their own networks. For example, they can force a disconnection by removing a network suggestion, manage Passpoint networks, receive more information about the quality of connected networks, and other management changes.
- Passpoint enhancements - Android now enforces and notifies about expiration date of a Passpoint profile, supports Common Name specification in the profile, and allows self-signed private CAs for Passpoint R1 profiles. Connectivity apps can now use the Wi-Fi suggestion API to manage Passpoint networks.
Image and camera improvements
- HEIF animated drawables - The ImageDecoder API now lets you decode and render image sequence animations stored in HEIF files, so you can make use of high-quality assets while minimizing impact on network data and apk size. HEIF image sequences can offer drastic file-size reductions for image sequences when compared to animated GIFs. Developers can display HEIF image sequences in their apps by calling decodeDrawable with an HEIF source. If the source contains a sequence of images an AnimatedImageDrawable is returned.
- Native image decoder - New NDK APIs let apps decode and encode images (such as JPEG, PNG, WebP) from native code for graphics or post processing, while retaining a smaller APK size since you don’t need to bundle an external library. The native decoder also takes advantage of Android’s process for ongoing platform security updates. See the NDK sample code for examples.
- Muting during camera capture - apps can use new APIs to mute vibration from ringtones, alarms or notifications while the session is active.
- Bokeh modes - Apps can use metadata tags to enable bokeh modes on camera capture requests in devices that support it. A still image mode offers highest quality capture, while a continuous mode ensures that capture keeps up with sensor output, such as for video capture.
Low latency
- Low-latency video decoding in MediaCodec -- Low latency video is critical for real-time video streaming apps and services like Stadia. Video codecs that support low latency playback return the first frame of the stream as quickly as possible after decoding starts. Apps can use new APIs to check and configure low-latency playback for a specific codec.
- HDMI low-latency mode - Apps can use new APIs to check for and request auto low latency mode (also known as game mode) on external displays and TVs. In this mode, the display or TV disables graphics post-processing in order to minimize latency.
Get started with Android 11
The Developer Preview has everything you need to try the Android 11 features, test your apps, and give us feedback. To get started, download and flash a device system image to a Pixel 2 / 2 XL, Pixel 3 / 3 XL, Pixel 3a / 3a XL, or Pixel 4 / 4 XL device. Additionally, you can set up the Android Emulator through Android Studio. The Android Emulator running Android 11 system images includes experimental support to run ARM 32-bit & 64-bit binary app code directly on 64-bit x86 Android Emulator system images. Lastly, for broader testing, GSI images are also available.
Next, update your Android Studio environment with the Android 11 Preview SDK and tools - you can do this from inside Android Studio. See the setup guide for complete details. To take advantage of the latest Android Studio features, we recommend installing the latest version of Android Studio from the canary channel.
When you’re set up, here are some of the things you can do:
- Try the new features and APIs - your feedback is critical during the early part of the developer preview. We’re actively looking for your input on our new APIs, while there’s still time for use to make changes. For more on what’s new, check out the API overview, API reference, and diff report. Please let us know your feedback and requests as soon as possible!
- Test your current app for compatibility - the goal here is to learn whether your app is affected by default behavior changes in Android 11. Just install your current published app onto a device or emulator and test all of the app flows. If you find issues, we recommend updating your app soon.
- Test your app with opt-in changes - Like in previous releases, Android 11 has opt-in behavior changes that only affect your app when it’s targeting the new platform. It’s extremely important to understand and assess these changes early. To make it easier to assess the impact, you can now toggle the changes on and off individually. As you test, please make sure to let us know how these changes are working for your app.
For more information, visit the Android 11 developer site. You’ll find an overview of what’s new in this release, details on behavior changes, setup and migration guides, release notes, feedback channels, and more.
Preview updates
We plan to update the preview system images and SDK regularly throughout the Android 11 release cycle. This initial preview release is for developers only and not intended for daily or consumer use, so we're making it available by manual download and flash only. Downloads are here and instructions are here.
As we get closer to a final product, we'll be inviting consumers to try it out as well, and we'll open up enrollments through Android Beta at that time. Stay tuned for details, but for now please note that Android Beta is not currently available for Android 11.
Give us your feedback!
As always, your feedback is crucial, so please let us know what you think — the sooner we hear from you, the more of your feedback we can integrate, and because of timelines, we’re giving priority to input we receive in the next several weeks. When you find issues, please report them here.


 Posted by the Google for Games Team
Posted by the Google for Games Team