Posted by Cheryl Lindo Jones, Mobile App Solutions Consultant, Google Play
As more Chromebooks are enabled with Google Play, now is a great time to optimize
your Android app for Chromebooks to reach a larger audience. The changes
made to optimize for large screens will benefit mobile devices that are able to
project to desktop monitors, like the Samsung Galaxy S8. The current
list of Chromebooks that can access the Play Store continues to grow.
There are several differences to consider when optimizing your Android app or
game for Chromebooks:
- Larger screen sizes and higher resolutions
- Multi-window and resizable-window support
- Different hardware input methods: keyboard, trackpad, mouse, stylus
- Convertible Chromebooks enabling use in laptop and tablet modes
Chromebook users can change screen resolutions, switch between various input
methods, and convert from laptop to tablet mode at any time, so Android apps and
games should handle all of these situations gracefully.
Discoverability on Google Play
If Android apps or games require hardware not available in a Chromebook (like
cellular capability or GPS), those titles will not show up on Google Play for
Chromebook users, similar to Play on Android tablets. Developers should maximize
discoverability on Google Play by doing the following:
Set requested permissions and uses-features in the manifest to ensure
compatibility with Chromebooks. Not all Chromebooks will have touchscreens,
GPS, or rear-facing cameras which are typical for smartphones. Update the
manifest so that sensors and hardware not commonly found on Chromebooks are not
required. Example:
<uses-feature android:name="android.hardware.touchscreen"
android:required="false" />
Additionally, to educate Chromebook users on any Chrome OS-specific features
that have been implemented, for example supporting additional input methods like
keyboard, trackpad, and stylus, or supporting large, high-resolution screens
with a responsive layout, developers should update the app description on Google
Play. It would also be useful to provide screenshots showcasing how well the app
or game works on the larger screen, or how the title works on a Chromebook
specifically.
Optimizing functionality
While most apps and games already work fairly well on Chromebooks without any
changes, it is still a good idea to explore how to provide an optimized,
consistent experience for Chromebook users.
Large screens and resizable windows
Chromebook users will be more inclined to multitask, opening multiple apps
and/or games at once, taking advantage of the screen size, and operating in a
manner consistent with a desktop or laptop form factor. Unlike on Android
phones, they can also change the screen resolution to fit more onto the screen,
or enlarge the fonts, UI, and graphics, if needed. Multi-window support and
fully resizable window support are key for this usage. Graphics, fonts, layout,
and touch targets should be adjusted accordingly as the screen resolution and
orientation changes.
It is also important to note that just because an app or game window is not in
focus, it does not mean that it is not visible. For example, if a video app is
open in an inactive window, it should continue to play content "in the
background" because it could still be visible along side another app window. To
fully support multi-window
usage in this case, pause video in onStop(), and resume in onStart().
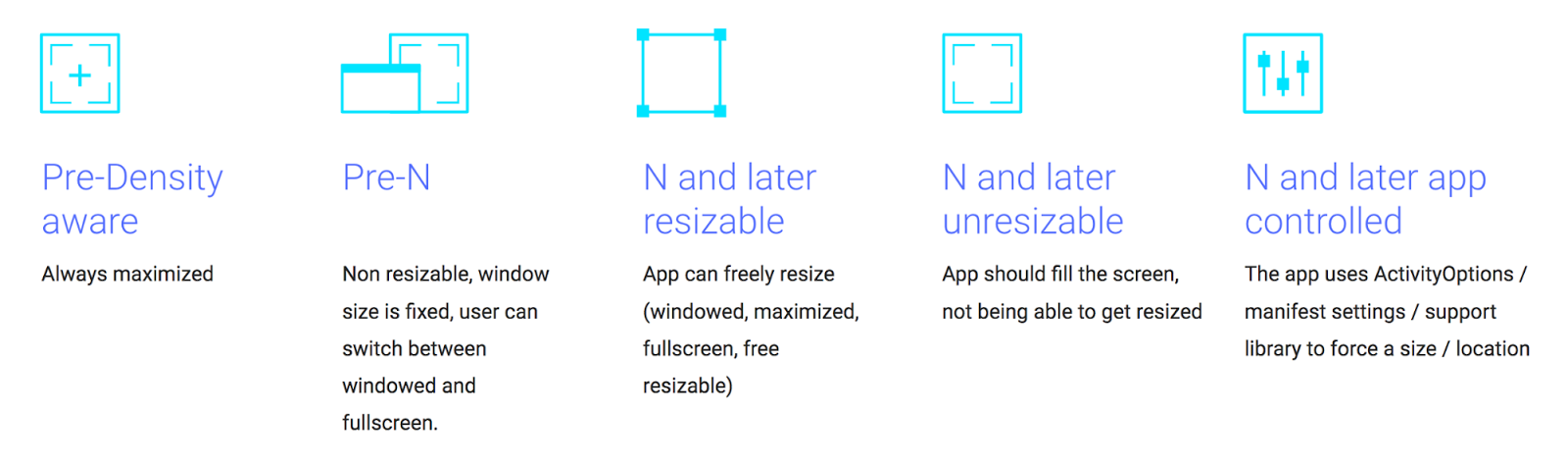
Targeting Android N (API level 24 and higher) will signal to the Chrome OS
window manager that compatibility restrictions should not be used. This allows
for more flexibility and control on the developer's part for supporting window
resizing.
The system will handle window
management best if Android N is targeted, but for pre-N API support, windows
can be toggled between either a default size selected at app launch, or a
full-screen mode with either the window bar visible, or with window UI hidden in
immersive full-screen mode.
When handling different windowing modes, it is important to know that the window
area for an app or game will be offset by the presence or absence of the window
control bar. The app should not assume that the activity will always be at (0,0)
in the window. Adjust the layout and touch targets accordingly. It is somewhat
common to see apps or games become unresponsive after a window resize or
orientation change because it did not gracefully handle the presence of the
window control bar, or the higher resolution settings of a Chromebook screen.
Orientation support
Because of the laptop form-factor, Chromebook users expect landscape to be the
default orientation for apps on Chromebooks. However, Android apps often assume
that portrait is the default orientation to support, due to the typical way
users interact with their smartphones. To offer flexibility to users, it is
highly recommended to support both portrait and landscape orientations. Some
Chromebooks are convertible, so users can change between laptop and tablet modes
at will, switching between portrait and landscape orientation, according to what
feels comfortable for a given use case.
Most importantly, if possible, do not require a restart if the orientation or
window size changes. If a user is in the process of filling out a form, creating
or editing some content, or in the middle of a level in a game and loses
progress because of an window change -- intentional or not -- it would be a poor
user experience.
Developers can monitor window configuration changes using
onConfigurationChanged() and dynamically handle those changes by adding this
line to the activity's manifest:
android:configChanges="screenSize|smallestScreenSize|orientation|screenLayout".
If it is absolutely necessary to require a restart upon changes to the window,
at least restore state by using the onSaveInstanceState() method so that work or
state is not lost.
Additionally, it is important to be consistent with the app's orientation as the
user is navigating through activities. Currently, the system forces Android apps
to follow the orientation of the root activity to help maintain consistency.
However, this may result in a situation where, perhaps an app starts out in
landscape orientation, and a login screen normally laid out for portrait
orientation pops up, and now does not look optimized due to an unresponsive
layout. Also, it is still possible to have a case where a springboard activity
starts out in an orientation that is different from the primary orientation of
the app. Please keep these possible scenarios in mind when designing the layout
for activities.
Finally, developers should be aware of the differences in handling cameras and
orientation on Chromebooks. Obviously, Android phones have front-facing and
rear-facing cameras that are situated at the top of a portrait-oriented screen.
The front-facing cameras on Chromebooks are situated at the top of a
landscape-oriented screen. Many Chromebooks do not have rear-facing cameras. If
an app requires a camera, it would be best to use android.hardware.camera.any to
access the front-facing camera, if a rear-facing one is not available. Again,
developers should target Android N and, if possible allow the app to be
resizable so that the system can take care of properly orienting the camera
previews.
Supporting multiple input methods
Chromebook users are used to interacting with webpages and apps using a keyboard
and trackpad. Effectively supporting these two input methods for an Android app
means:
- Supporting hotkeys for commands that a desktop app user may be familiar with
- Using arrow and tab keys and a trackpad to navigate an activity
- Allowing hover and opening context menus
- Supporting other trackpad gestures to enhance productivity in desktop/laptop
mode
Something as simple as hitting return to send text in a messaging app, or
allowing a user to navigate fields by hitting the tab key will make an app feel
more efficient and cohesive on a Chromebook.
While there is a compatibility
mode for Chrome OS to emulate touchscreen scrolling and other touch events,
it would be best to optimize an Android app by declaring
<uses-feature
android:name="android.hardware.type.pc"
android:required="false" />
in the manifest to disable compatibility mode in order to further define custom
support for keyboard and trackpad.
Similarly, the system can guess at giving focus to the right views when
navigating via the tab or arrow keys on a keyboard. But for best performance,
specify how keyboard navigation should be handled
in the activity manifest using the android:nextFocusForward attribute for
tab navigation, and android:nextFocusUp, android:nextFocusDown,
android:nextFocusLeft, android:nextFocusRight attributes for arrow key
navigation.
On a related note, some Chromebooks do not have touchscreens, therefore
well-optimized Android apps on Chrome should not assume the user can perform
typical swipe and multi-touch tap gestures to navigate through an app or game.
If primary functionality cannot be performed using only a keyboard or trackpad,
the user experience will be severely impacted on non-touchscreen Chromebooks.
Try to "translate" existing touchscreen tap and swipe gestures into something
that can be easily done on a trackpad or using the keyboard.
Newer Chromebooks are gaining stylus support, allowing for richer interactions
for sketchbook and note-taking apps, photo editors, games, and more. Developers
are encouraged to use available
APIs to support pressure-sensitivity, tilt, and eraser inputs. To enable
users to comfortably rest their hands on the screen while writing, drawing, or
playing games with the stylus, support palm rejection. The system will attempt
to ignore input from a user's resting palm, but in case such erroneous touch
events are registered, Android apps should gracefully handle ACTION_CANCEL
events to erase the erroneous inputs.
By supporting all of these additional input methods, users will be able to take
full advantage of the laptop mode for Chromebooks to work more efficiently, or
to be more creative.
Learn more
While a lot was covered in this article, we have additional resources for you to
learn more about optimizing their apps and games for Chromebooks. Read our Medium post
with tips to get your app running great on Chromebooks and watch our
session at Google I/O 2017, Android Apps for Chromebooks
and Large Screen Devices. There is also training material on the Android
developers website for building apps for
Chrome OS. If you have any questions, reach out to the Android developer
community and post with the hashtag #AndroidAppsOnChromeOS.
How useful did you find this blogpost?
★
★
★
★
★