Earlier today, we kicked off our 10-year celebration of hosting developer events with Google I/O in front of over 7,000 developers at Shoreline Amphitheatre, and with millions of other viewers on the I/O live stream around the world. During the keynote, we had a number of announcements that featured tools for Android, iOS, and mobile Web developers, showcased the power of machine learning for delivering better user experiences, and introduced a previewed platform for high quality, mobile virtual reality.
And over the next three days at the festival, we’ll continue to focus on things that matter to you: Develop, to build high quality apps; Grow & Earn, to find high quality users, increase user engagement and create successful businesses; and What’s Next, a look at new platforms for future growth.
Develop, Grow & Earn with Firebase
Those core themes are best represented in our launch of Firebase. As shared during the keynote, we’ve significantly expanded Firebase beyond a mobile backend to include brand new features, like mobile analytics, growth tools, and crash reporting. Firebase is now a suite of 15 features and integrations designed to help you develop your app, grow a user base and earn money. At the heart of the suite is a new mobile analytics tool we built from the ground up called Firebase Analytics. Available for free and unlimited usage, Firebase Analytics is inspired by our decade-long experience running Google Analytics, but designed specifically for the unique needs of apps.Let's also take a closer look at the other major developer news at I/O:
Develop
- Android N Developer Preview 3 — Get a look at the next release of Android N focused on performance, productivity and security. Even better, Android N is now ready to test on primary phones or tablets.
- Android VR — A rework of the entire Android stack in N to tailor it to provide high quality mobile VR experiences.
- Android Studio 2.2 Preview — Our new preview focuses on speed, smarts, and Android platform support. This major update includes a completely rewritten, feature-rich Layout Designer.
- Android Wear 2.0: A developer preview of the biggest platform update since we launched Android Wear two years ago. It includes updated design guidelines and APIs that make the watch even more useful for watch faces, messaging, and fitness. Apps on the watch can now be standalone, with direct network access to the cloud.
- Recording APIs: enables Android TV app developers and content providers to bring recording functionality to live channels.
- Google Play services 9.0 — In addition to Firebase, the next release includes new API updates for Ads, Nearby and Play Games services.
- Android Pay APIs — A new set of tools that includes support for mobile web, Instant Apps, Save to Android Pay and an API for issuers. We’ll have more to share during the session “Android Pay everywhere: New developments” later today at 2:00 PM PT Stage 1 Hercules.
- Progressive Web Apps — A new set of capabilities to build app-like mobile websites that work reliably on the worst network connections and can send notifications to re-engage users.
- Credentials API — The latest version of Chrome now supports the Credential Management API, allowing sites to interact with the browser’s credential manager to improve the sign in experience for users. The API enables users to sign in with one tap and lets them automatically sign back in when returning to the site.
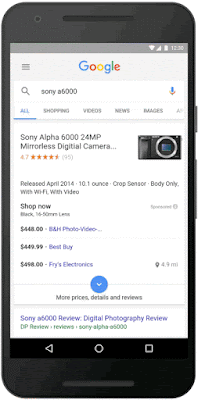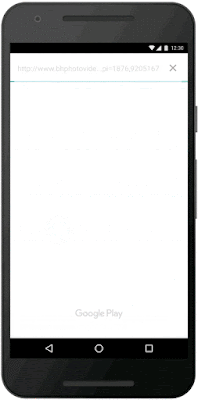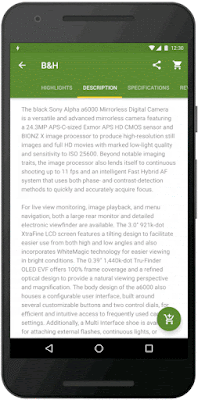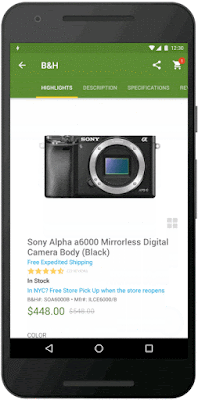
- Accelerated Mobile Pages — Check out the AMP project, an open source initiative that is helping publishers create mobile-optimized content once and have it load instantly everywhere.
Grow & Earn
- Reach a global audience on Google Play — New and powerful tools to help you grow your business: discover and join beta tests from the Play Store (including a new Early Access section), discover collections of complementary apps to help users solve complex tasks, see how your app runs on real devices with a new pre-launch report, get insights and benchmarks for reviews and user acquisition, monitor your app stats and get notifications when your updates are live with the new Play Console app, and more.
- Android Instant Apps — With Android Instant Apps, users can open your app simply by tapping on a link, even if they don’t have the app installed. Instant Apps is compatible with Android Jelly Bean and later, reaching over a billion users. We’re working with a small set of developers now, and we’ll be gradually expanding access.
- Building for billions — New resources to help you optimize your app and get your business ready to serve over a billion Android users around the world.
- Universal App Campaigns — Last year, we introduced Universal App Campaigns as a simple and powerful way to surface apps to the billions of users across Google Play, Search, YouTube, and the Google Display Network. We’re building on this success by expanding onto iOS and by helping developers use insights to optimize for lifetime value. See our new apps best practices.
What’s Next
- Awareness API: We'll be previewing a new, unified sensing platform that enables apps to be aware of all aspects of a user's context, while managing system health for you. Learn more at the "Introducing Awareness API: an easy way to make your apps context aware" session later today at 3:00 PM PT in Stage 5 Libra.
- Daydream — We’ll have more to share on how developers can start building Daydream apps during the “VR at Google” session tomorrow (May 19) at 9:00 AM PT in the Amphitheatre and livestreamed.
- Chromebooks — Hear from the team firsthand what’s new with Chromebooks tomorrow (May 19) at 11:00 AM PT in Stage 8 Crater.
- The Mobile Web — We’ll share what we’re doing to improve the mobile web experience for developers and users tomorrow (May 19) at 2:00 PM PT in the Amphitheatre.